Monitor Palo Alto firewalls
Network Insight for Palo Alto firewalls automates the monitoring and management of your Palo Alto infrastructure to provide visibility and help ensure service availability.
For Palo Alto firewalls, you'll find the following subviews:
- Site-to-Site VPNs: Review names of tunnels, status, failure reason message, IN/OUT transferred data, encryption, hashing, virtual system, security zone, and local and peer IP addresses
- GlobalProtect VPNs: Review username, public IP, virtual IP, time of the connection, status, and transferred data
Requirements
| Requirement | Detail |
|---|---|
| REST API access | You need valid credentials to poll Palo Alto devices through REST API. |
| Log at Session End |
To poll Global Protect throughput data, Log Settings in the Action tab for Security Policy Rule must be configured to Log at Session End. |
| Palo Alto account permissions |
To access the statistics, you need an account with the administrator role and the following permissions set for the XML API:
|
How to monitor Palo Alto devices
To access the Site-to-Site VPNs and Global Protect VPN subviews, add the device to NPM for monitoring or enable polling for Palo Alto data on devices already monitored in NPM.
To access the device, NPM calls the device and requests a REST API key, also known as "session key". NPM then accesses the device through the key, not through the credentials directly.
A change of credentials on the firewall can thus lead to issues because NPM needs not only the credentials, but also the session key to poll the data. When you change credentials on the firewall, go to the Edit Node page and change credentials in NPM.
For Palo Alto devices, NPM provides the Site-to-Site tunnel down out-of-the-box-alert. You can configure custom notifications based on Palo Alto events and custom reports showing statistics relevant for Palo Alto devices.
Add Palo Alto devices and enable Palo Alto polling
Add Palo Alto devices for monitoring.
You need Node Management Rights. See Define what users can access and do.
- Click Settings > All Settings, and click Add Node in the Getting Started grouping.
- Enter the IP address for the device.
- Select Most Devices: SNMP and ICMP as the polling method.
If you only need information about tunnels, you can choose ICMP here. If you also want to see data about the Palo Alto node itself, such as traffic, CPU, or memory, select SNMP.
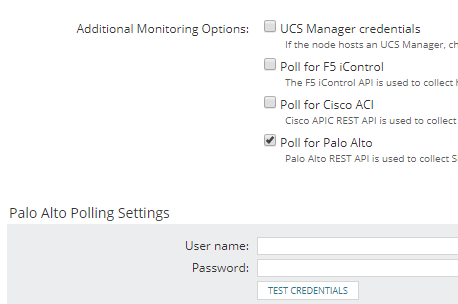
- Scroll down to Additional Monitoring Options, and select Poll for Palo Alto.
- Provide the credentials for accessing the Palo Alto device and click Test Credentials.
If the certificate is not validated successfully, for example if it is a self-signed certificate, use a different certificate, or click Accept Certificate to approve the certificate.
- Complete the Add Node wizard.
NPM now polls Palo Alto details, and you can access the Palo Alto subviews for the device. The polling frequency is the Default Node Statistics Poll Interval and is 10 minutes by default.
Enable polling for Palo Alto on a monitored node
Palo Alto firewalls are polled using REST API to collect Site-to-Site and GlobalProtect VPN information.
- Click Settings > Manage Nodes.
- Select the node, and click Edit Properties.
- Enable Palo Alto polling:
- Scroll down to Additional Monitoring Options, and select Poll for Palo Alto.
- Provide the credentials for accessing the Palo Alto device and click Test Credentials.
- Click Submit.
NPM now polls Palo Alto details, and you can access the Palo Alto subviews for the device.
View Site-to-Site tunnels on a Palo Alto firewall
By default, NPM polls data every ten minutes using several different polls. At first, NPM polls a list of all entities, and then NPM polls additional data for each entity.
NPM polls static properties, and calculates bandwidth consumption based on the total amount of bytes coming through the firewall.
If connectivity issues happen during polling, partial details can be displayed.
The following table captures how statuses polled on Palo Alto devices are displayed in Orion:
| Palo Alto status | Orion status | Value |
|---|---|---|
| Active | Up | 1 |
| Inactive | Down If the tunnel is down in NPM, it's inactive in Palo Alto. |
2 |
| Init |
Inactive |
24 |
| Other statuses | Unknown | 0 |
Tunnels are constructed between two firewalls. If NPM discovers that it is monitoring the same tunnel from another firewall, just another side of it, and the node is also monitored with NPM through REST API, you can click the underlined IP address to access the node details view.
To get historical data for monitored tunnels, select up to three tunnels, and click Performance Analyzer to open the tunnels in PerfStack.

View the GlobalProtect VPN subview
To display a list of active sessions on your Palo Alto firewall, go to the node details view, and click the Global Protect subview.
The subview displays a record for each session. When the session ends, you can see the end time for it. When a session is renewed, it is displayed as a new session in the Global Protect list.
NPM keeps the history of Global Protect sessions for two days. When a session is connected, you can see the following details:
- Public IP provided by the service provider
- Virtual IP provided by the firewall

PerfStack
In Performance Analysis dashboards, you can search for Site-to-Site entities and display the following metrics for them:
- Availability
- InBps
- OutBps
Access Palo Alto data in PerfStack
- Go to PerfStack by clicking My Dashboards > Home > Performance Analysis.
- Search for Palo Alto entities and metrics.
Access Palo Alto data in PerfStack from Palo Alto views
- Go to the node details view for your Palo Alto firewall.
- Select up to three tunnels in the Site-to-Site or GlobalProtect VPN subview, and click Performance Analyzer.

Intelligent Maps
You can display Palo Alto firewalls on Intelligent Maps.
Troubleshooting
Failure reason is not accurate
When a Site-to-Site tunnel is down, you can see the reason. This information is polled from traffic logs, based on the last message indicating failure. Whereas this can help you understand your issue, there might be issues. These issues might be caused by the asynchronous nature of polling, NPM might get various information, not related to the current issue.
My Global Protect session is displayed as "ended" although it is active
When a session connecting remotely to the office fails, NPM informs you that it ended and records the end time. If you renew the session, it appears in the Global Protect VPNs subview as a new session.
