Work with client certificates in WPM recordings
You can use the Web Transaction Recorder to create recordings that check for valid client certificates. When you record a sequence of steps that navigates to a page with a certificate, you're prompted to select a certificate for that step.

When you select a certificate, WPM stores the following data in an authentication binding that is saved within the recording:
- The URL for the secured page (or portion) and,
- The Common Name (CN) property of the certificate.
After you link a certificate to a recording, a Key icon appears at the top of the Recorded Steps pane. Click the Key icon to display certificates related to the recording and any other type of authentication that was applied. Click the Options (![]() ) icon to see available commands for each row, as shown here:
) icon to see available commands for each row, as shown here:

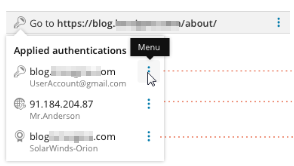
A single step can include multiple types of authentication, as shown here. Click the Options (![]() ) icon to display available commands for that row, such as Edit or Delete.
) icon to display available commands for that row, such as Edit or Delete.
Note the following details about working with certificates in WPM recordings:
- This feature is not supported in recordings used for Transaction Monitoring in Pingdom.
- Unlike the Deprecated WPM Recorder, the latest Web Transaction Recorders do not save certificates in recordings. Install a client certificate in the personal certificate store for each WPM Player service account used by the WPM Player service on remote systems where transactions are played back. You can also use a Group Policy Object (GPO) to install certificates, and then use domain accounts for playback.
- Playback fails if the hostname for a secured page changed and WPM cannot match it with the URL property of the binding. Remove the original binding and create a new binding instead. You may need to recreate the entire recording.
- If playback fails on a remote system that has no certificates installed, WPM will not prompt you to select a required certificate. Install at least one certificate, even if it's not the certificate the recording requires.
Removing a step where authentication was applied may render later steps and actions inaccessible, which will block playback. It may be easier to start over with a new recording.
Create recordings for websites without valid certificates
Many WPM tools are designed to be flexible so you can apply them to a variety of situations. For example, you can use text validation or Image Match in a recording to check for either a positive or negative result.
Similarly, you can create various recordings that test how certificates are handled, as described in the following examples:
- Check a certificate and only proceed to the next step after a positive result. You can then create transactions based on the recording that are hosted on remote machines without valid certificates to test how a website handles invalid certificates.
- Check a certificate and then block playback due to a negative result.
- Check a certificate, determine it is invalid, and then add a step to simulate a user that trusts the certificate anyway (for example, a self-signed certificate on a device management page).
- Skip Certificate Authority (CA) validation for a self-signed certificate.
To support playback of recordings with self-signed, expired, or invalid certificates on remote systems, add sites to the Hosts file stored in the following default location:
C:/Windows/System32/drivers/etc/hosts
You can use this same technique on remote systems that host the WPM Player service, to support playback of any transactions that are based on recordings that meet the same criteria.
To prepare a remote system for recordings that test certificates:
- Add the IP address and system name of the page that requires a certificate to the hosts file on the remote system. For example, a row might look like the following:
10.123.45.71 ENG-AUS-SYS-123 - Download or copy the certificate file to the remote system that hosts the Web Transaction Recorder.
- Use the Certificate Import Wizard in the Microsoft Management Console (MMC) to create a certificate for the page.
- Install the certificate for the page.
To create a Chromium whitelist:
- On systems that host the WPM Recorder and WPM Player, add this key to the registry:
HKLM\Software\Policies\Google\Chrome\AuthServerWhitelist - Append the registry key with the website URL, as shown in this example:
HKLM\Software\Policies\Google\Chrome\AuthServerWhitelist="www.solarwinds.com"
Note the following details about creating whitelists:
- Sites entered in the whitelist of the config file on the location are excluded from Certificate validation
- Use a certificate's CN as the Site parameter for the whitelist.
- If necessary, separate multiple CNs in the whitelist with commas or colons.
Restart remote machines after adding or changing a Chromium whitelist.
