SAML Migration
Navigation Notice: When the APM Integrated Experience is enabled, Loggly shares a common navigation and enhanced feature set with other integrated experience products. How you navigate Loggly and access its features may vary from these instructions.
Last updated: April 19, 2021
Loggly was updated with enhancements related to user management and SSO/SAML for Corporate single sign-on. These updates require Loggly SAML customers to migrate from the previous, Loggly-based SAML authentication to the new SolarWinds-based SAML authentication. This document describes the steps taken to transition Loggly from the old method of SSO/SAML to the new method.
Thank you for being a Loggly customer and—as always—we sincerely value your feedback. If you have any questions, please e-mail Loggly support.
For organization owners
We
This migration delivers you the following benefits as a Loggly SSO/SAML customer:
- Access to the new Log Volume Dashboards for all users
- SAML Role Mapping UI (removing the need to contact support for changes)
- SAML Service Accounts (allowing accounts to log in via SolarWinds Unified Login credentials, not via SAML)
- New, combined navigation with simplified user management across all products
- Ability to use other products in the APM Integrated Experience portfolio with a single organization
Migration to the new SSO/SAML is a prerequisite to taking advantage of some new, powerful Loggly features.
Actions required
We already migrated your settings from the previous, Loggly-based SAML to the new SolarWinds-based one. For the organizations that did not manually activate the new SAML, we
These actions must be performed for each organization for which you are an organization owner. To access your other organizations, click your profile icon.
-
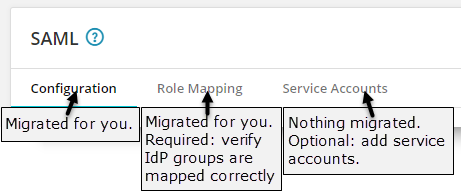
Mandatory - Verify and Enable Role Mapping settings. Go to your organization's SAML Role Mapping settings and verify that the IdP groups in the Organization Roles and Product Roles fields for Loggly and any other products your organization uses are correct. After verifying settings, click to enable Role Mapping.
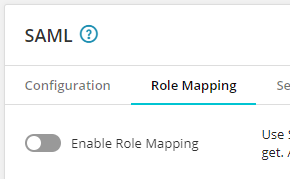
See Set up role mapping for details.
-
Optional - Set up service accounts. To allow users to log in using the username and password, in the organization's Security settings click Service Accounts and add the users in the field provided. See Set up service accounts for details.
-
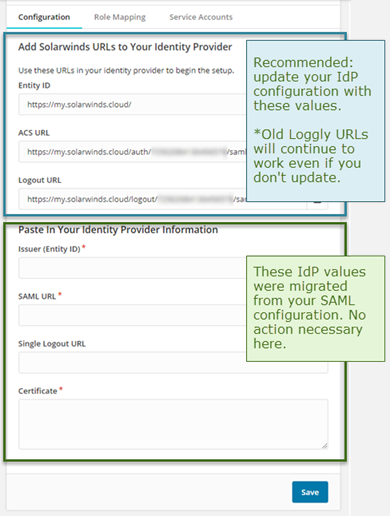
Optional - Update your IdP configuration. We recommend that you update your IdP configuration with the new SolarWinds URLs shown in the Entity ID, ACS URL, and Logout URL fields in the SAML Configuration tab. After you update your configuration, log in from the IdP side first to propagate updates correctly.
While we recommend that you update your IdP configuration with the new SolarWinds URLs, it is not required at this time. Your existing configuration with the Loggly URLs will continue to work.
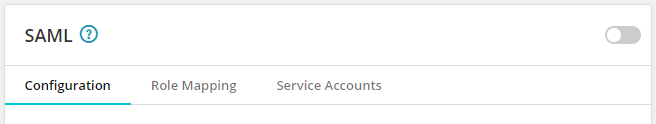
If the new SAML was not enabled for you, after you’ve validated the settings, save any changes you've made and activate the new SAML by clicking the toggle on the right side of the SAML pane.
See Configure Single Sign-On (SSO) via SAML for information detailing the new SAML configuration in Loggly.
As part of the enhanced security requirement, we sent an email to some SAML users requesting them to reset their password on or before March 8, 2021. If they didn't reset their password by that time, we reset their password.
For Loggly SSO/SAML users
As part of our continuing enhancements to Loggly as well as the remainder of the SolarWinds APM Integrated Experience products (SolarWinds AppOptics and SolarWinds Pingdom), we
This migration delivers you the following benefits as a Loggly SSO/SAML customer:
- Access to the new Log Volume Dashboards for all users
- New, combined navigation with new user management across all products
- Ability to use other products in the APM Integrated Experience portfolio with a single Organization
Migration to the new SSO/SAML is a prerequisite to taking advantage of some new, powerful Loggly features.
If you are a member of one organization
As a result of the migration to the new common SSO/SAML, there
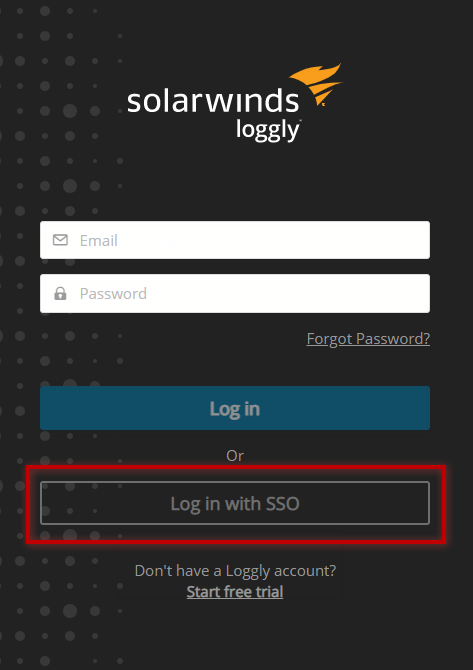
Instead of the previous login, which asked you if you wanted to sign in with your “corporate login,” you
If you would like to log in with the SolarWinds Unified Login (previously called a local account) using a username and password, you need to contact your organization owner and ask them to add you as a service account.
If you are a member of multiple organizations
As a result of the migration to the new common SSO/SAML, there

Instead of the previous login, which asked you if you wanted to sign in with your “corporate login,” you
Since you are a member of multiple organizations, you will be prompted to authenticate for each of your organizations via username and password and/or IdP.
If you would like to log in with the SolarWinds Unified Login (previously called a local account) using a username and password, you need to contact your organization owner and ask them to add you as a service account.
If your account needed to be verified with a password reset
As part of this migration, some accounts had to be verified. These users received an email on February 22, 2021, requiring them to reset their passwords to continue using Loggly. If they logged into Loggly, a banner appeared about the need to reset passwords. If you did not reset your password, we started the process for you. You will not be able to log in until you reset your password using the reset password page.
If you did not receive an email and can log into Loggly successfully, no action is required.
FAQs
General
What is SSO/SAML?
Single sign-on (SSO) is an authentication method that allows users to log in to several independent software systems with a single set of credentials. Security Assertion Markup Language (SAML) is a protocol used to configure and implement SSO. This (single) authentication is provided by an identity provider. After the user is authenticated against the identity provider, they are automatically authenticated to use all configured services. This helps administrators manage users' access to multiple services and allows users to access multiple services without worrying about multiple login credentials.
In layman's terms, SSO/SAML allows users to access multiple software systems, including Loggly, using their corporate login method.
When the term SAML is used in this document or in the software, it is referring to the SAML authentication method used by Loggly to implement SSO.
What is an IdP?
IdP stands for identity provider, which is a service that stores and manages user accounts. Identity providers allow companies to securely manage access to their systems and data. SSO/SAML uses an identity provider to authenticate user accounts across multiple services.
Examples of identity providers include Microsoft Azure, Google, OneLogin, and Okta.
Organization owners
What are Organization Roles and Product Roles?
Organization Roles define the access users have to an organization’s settings and resources across SolarWinds Application Management products (AppOptics, Loggly, Papertrail, and Pingdom). Organization Roles take precedence over Product Roles.
- Member roles can view the organization’s resources, but cannot modify settings related to the organization.
- Admin roles can also manage the organization, its users, the products activated, and the organization’s settings.
- Owner roles can do anything a member or admin can do, but can also configure Security settings.
If a user or group is assigned to multiple roles, the role with the greatest access will be applied.
Product Roles define the access users have to the individual product's data and settings. For Loggly, the user role has access to log data. Depending on the restrictions applied to the user in Loggly settings, access to that data may be limited to a set of specific source groups. An admin in Loggly can access all log data, as well as manage users and account settings. The owner role can also update billing details, modify subscription settings, and cancel the Loggly organization.
What do I put in the Loggly owner role?
Loggly owners have access to Loggly billing details, can modify subscription settings, and can deactivate Loggly for the entire organization. If the group mapped to the admin role needs to modify those settings, you can map the same group to the owner role. Otherwise, create a separate group for your Loggly owners in your identity provider and assign the correct users to the new group.
What is being migrated and where is it being migrated?
We migrated all SSO/SAML users and SAML configurations from the Loggly-specific SAML authentication to our new common SolarWinds SAML authentication. Your previous role mapping settings were migrated as well, though you will need to review the mappings to ensure that the correct people or groups have been assigned the owner role.
What happens if I don't do anything?
If you are an owner and you do not follow the instructions here, we will complete the process for you. Your organization will use the new SAML authentication with the configuration and role mapping settings that will be automatically migrated from your previous SAML settings.
However, we will not update your IdP configuration; it will still point to the old Loggly SAML URLs. The IdP configured settings will continue to work, but eventually we will stop supporting the old Loggly SAML URLs. We recommend that you:
- Update your IdP settings to use the new SolarWinds URLs
- Verify all Loggly SAML settings, especially with respect to role mapping
If you are an owner and you did not follow the instructions provided via email or listed on this page previously, we completed the process for you. Your organization is using the new SAML authentication with the configuration and role mapping settings that were automatically migrated from your previous SAML settings.
However, we will not update your IdP configuration; it will still point to the old Loggly SAML URLs. The IdP configured settings will continue to work, but eventually we will stop supporting the old Loggly SAML URLs. We recommend that you update your IdP settings to use the new SolarWinds URLs and verify all Loggly SAML settings are as desired, especially with respect to role mapping.
What happens
With the new SAML authentication, your users experience a new flow when logging into Loggly (see For Loggly SSO/SAML users) and your organization can take advantage of the benefits to the new SAML authentication.
Can I opt out of the new SAML authentication and keep using the old Loggly-specific SAML authentication?
Not really. You can temporarily disable the new SAML authentication if you experience issues with new SAML authentication, which would switch you to the old Loggly-specific SAML authentication. Please contact Support so we can resolve your issues and you can use the new SolarWinds SAML authentication.
However, you cannot remain on the legacy Loggly-specific SAML authentication forever. To deliver a common, simplified, and SAML authentication for customers using any combination of the SolarWinds APM Integrated Experience products, we require all Loggly users to migrate to the new SAML authentication.
The new SAML also allows you to take advantage of new, powerful Loggly features.
Can I permanently disable SAML authentication?
If you want to disable the SAML authentication permanently, contact our support team.
Why are my organization's users asking for me to create service accounts for them? Should I do it?
Service accounts allow users to log into Loggly with a username and password instead of using the SAML-authentication method you have set up. Whether or not you create a service account for a user depends on the following:
-
Do you need to audit user access to a product? Disallowing service accounts allows you to audit login access from one location - your IdP.
Organization owners can log in without SAML, so you may still need to track their non-SAML logins.
-
How much manual user management and support are you willing to perform? Creating a service account for users means paying attention to which users can log in with only SAML versus those that can log in via either SAML or username and password. Also, when revoking a user's access to Loggly, you must remove them from both the IdP and the list of service account users; if a user is no longer a member of an IdP but has a service account defined, they still can access Loggly.
-
Do you need to grant users not in your company's IdP access to your Loggly organization? Creating a service account for that user would allow these users to log into Loggly without authenticating against your company's IdP.
-
Does your user access multiple organizations? If each organization owner for that user's organizations allow the user to log in with the SolarWinds Unified Login credentials, that user can log in once to access all of their organizations.
Users
Why don't I see the new login page?
When the new SSO/SAML authentication method is activated, your login screen will update and your process for logging in will change as described above. Contact your organization owner to find out when they plan on activating the new SSO/SAML authentication.
When will my login screen change?
When the new SSO/SAML authentication method is activated, your login screen will update and your process for logging in will change as described above. Contact your organization owner to find out when they plan on activating the new SSO/SAML authentication.
What happens if I don't do anything?
If you were notified about resetting your password, you will need to reset your password to continue using Loggly.
If you were not notified about resetting your password, there is no action necessary. Your login process will change, but you do not need to do anything to activate this change.
Do I have to use single sign-on? Can I log in with a username and password instead?
If you want to log in with just a username and password, ask your organization owner to configure your user account as a service account. With a service account, you can log in with a SolarWinds Unified Login (previously called a local account) using a username and password.
I was removed from the identity provider organization and cannot log in. What should I do?
Please contact our support team to resolve the situation.
I am prompted to log in with an identity provider multiple times in a row. Why is this happening?
If you belong to multiple organizations with SSO/SAML enabled, you need to authenticate against each identity provider. If you are not already authenticated to all identity providers, you will be prompted to log in for each provider you are not logged into.
If you do not need access to each organization, contact our support team to discuss removing your account from the some organizations to reduce the number of organizations you log into. If you need access to all organizations but want to reduce the number of providers that you authenticated against, consider talking to each organization owner to see if they will create a service account for you instead, which would allow you to log into those organizations with your SolarWinds Unified Login instead of SSO/SAML.
I logged in with my identity provider but I am still prompted to enter my username and password. Why?
If you are a member of an organization that does not have SSO/SAML configured, you will need to log in to that organization with your SolarWinds Unified Login. If you did not have a password defined for your SolarWinds Unified Login user account, you will need to reset your password first.
I am a new user who was recently added to the IdP. When I log in with SSO, I see an error message and cannot log in. What should I do?
When accessing a SolarWinds Application Management product for the first time, new users need to log in from the IdP's portal page. Click the link to the SolarWinds product from your IdP's portal page to access the application. After this first access to the SolarWinds product, you can log in from the IdP page or via the Log in with SSO link.
