Java Log4j 1 Log Management
Loggly provides the infrastructure to aggregate and normalize log events so they are available to explore interactively, build visualizations, or create threshold-based alerting. In general, any method to send logs from a system or application to an external source can be adapted to send logs to Loggly. The following instructions provide one scenario for sending logs to Loggly.
You can send and manage your Java logs using Log4j version 1. We’ll show you how to setup a syslog appender to forward these to Rsyslog, which will then forward them to Loggly.
We automatically parse out the timestamp, method, fully classified class name, thread, and log level from log4j. The syslog protocol does not support multiline events, so rsyslog will combine them into a single line escaped by octal characters. The advantage of using Rsyslog is that it can send TCP events without blocking your application, can optionally encrypt the data, and even queue data to add robustness to network failure. We’ve also created a log4j-syslogwriter-64k library that supports up to events up to 64k in size so long stacktraces do not get truncated. Although the library supports to send logs up to 64K, currently you can only ingest up to 32K logs to Loggly. This guide assumes you use Java Log4j version 1.2 or higher, the default log configuration and directories. For alternatives, please see the Advanced Options section.
Java Log4j Log Management Setup
1. Configure Syslog Daemon
If you haven’t already, run our automatic Configure-Syslog script below to setup rsyslog. Alternatively, you can Manually Configure Rsyslog or Syslog-ng.
curl -O https://www.loggly.com/install/configure-linux.sh sudo bash configure-linux.sh -a SUBDOMAIN -u USERNAME
Replace:
- SUBDOMAIN: your account subdomain that you created when you signed up for Loggly
- USERNAME: your Loggly username
2. Configure Syslog Daemon for UDP Input
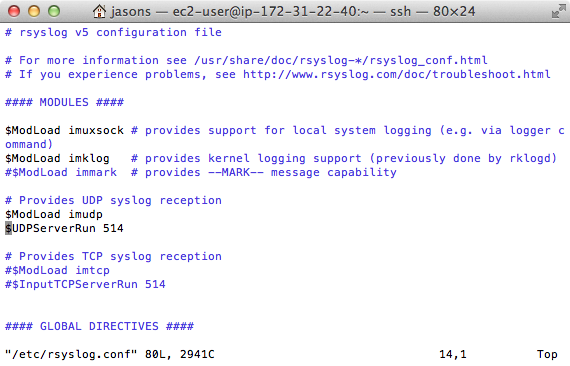
Open rsyslog’s configuration file
sudo vim /etc/rsyslog.conf
Uncomment these lines to accept UDP messages on the default port 514.
$ModLoad imudp $UDPServerRun 514
Restart the rsyslog service so the changes take effect
sudo service rsyslog restart
3. Log4j Configuration
Add Dependency in your pom.xml or Download jar file from maven
<dependency> <groupId>com.github.loggly.log4jSyslogWriter64k</groupId> <artifactId>log4jSyslogWriter64k</artifactId> <version>2.0.0</version> </dependency>
Then run maven to install
mvn clean install
Open your log4j.properties file:
vim log4j.properties
Configure SyslogAppender to write these messages as UDP over localhost to the syslog daemon. The daemon will forward them to Loggly. The first field in the conversion pattern is the syslog appname, in this case it’s set to java. If you are using an HTTP appender, you do not need to add an appname.
log4j.rootLogger=INFO, SYSLOG
log4j.appender.SYSLOG=com.github.loggly.log4j.SyslogAppender64k
log4j.appender.SYSLOG.SyslogHost=localhost
log4j.appender.SYSLOG.Facility=Local3
log4j.appender.SYSLOG.Header=true
log4j.appender.SYSLOG.layout=org.apache.log4j.EnhancedPatternLayout
log4j.appender.SYSLOG.layout.ConversionPattern=java %d{ISO8601}{GMT} %p %t %c %M - %m%n
Save the file then restart your Java application so the changes take effect.
4. Verify Events
Search Loggly for events with the java log type over the past hour. It may take a few minutes to index the event. If it doesn’t work, see the troubleshooting section below.
logtype:java
Click on one of the logs to show a list of Java or JSON fields (see screenshot below). If you don’t see them, please check that you are using one of our automatically parsed formats.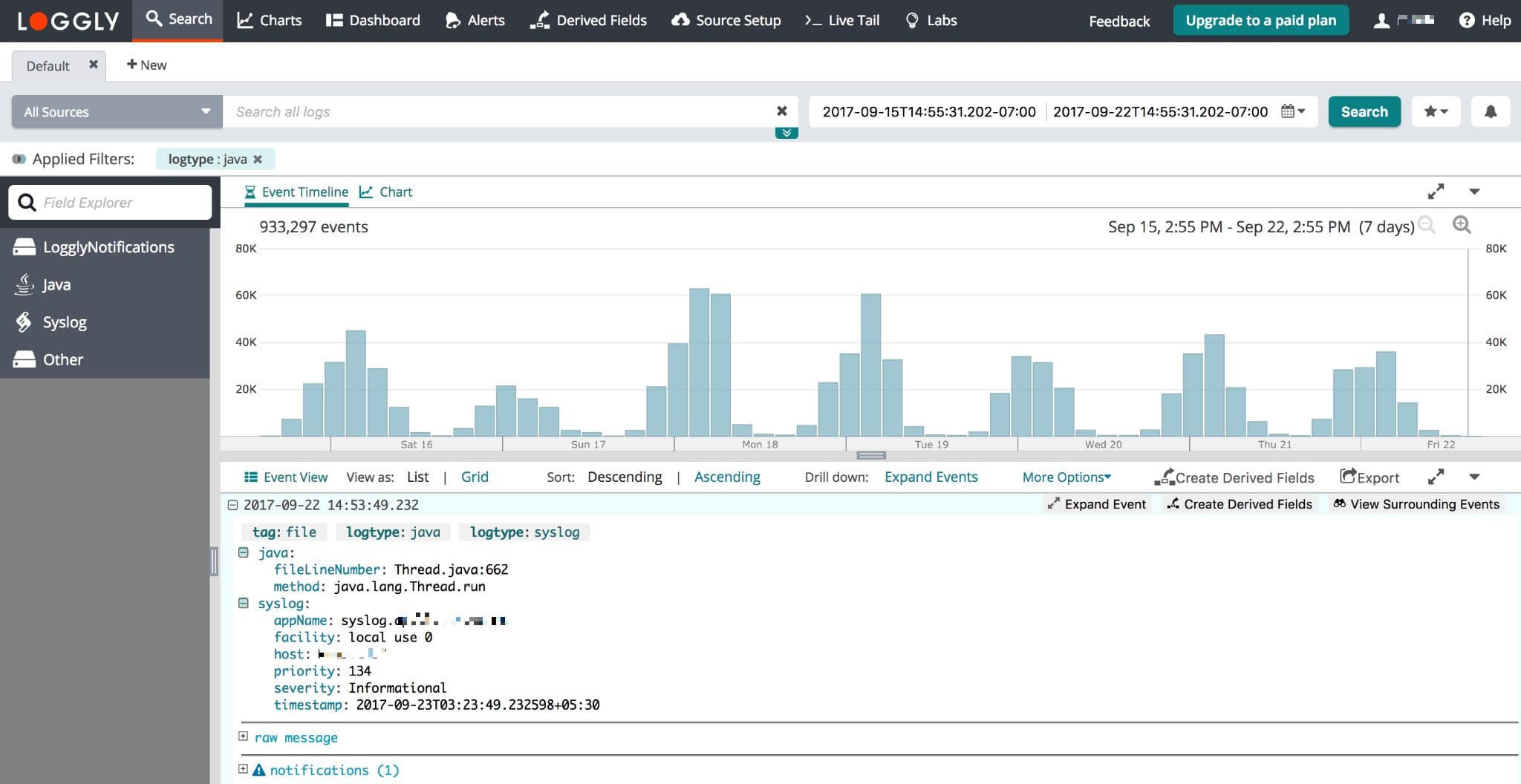
5. Next Steps
- Troubleshooting with Java Logs – Use your logs to find the most common exceptions, trace transactions, debug memory issues, and more.
Advanced Java Log4j Log Options
- Log4j2 – You can also send log using Java Log4j2
- File Monitoring – You can also configure Log4j with a FileAppender, then monitor that file using Rsyslog. This gives you a local backup but doesn’t work well with multiline stacktraces.
- CustomAppname– You can set custom appName in Log4j using following conversion pattern
log4j.appender.SYSLOG.layout=org.apache.log4j.EnhancedPatternLayout log4j.appender.SYSLOG.layout.ConversionPattern= CustomAppname %d{ISO8601}{GMT} %p %t %c %M - %m%n - Syslog4j – The Syslog4j appender can send events up to 64k in size, but it doesn’t seem to follow the layout pattern to enable parsing.
- logglylog4j – To send events directly to Loggly over the HTTP/S Event API, supports multiline with proper newline display
- Java Logback – For Logback or SLF4J logging
- Search or post your own log4j examples, configuration, log4j tutorials, or other questions in the community forum.
Java Log4j Troubleshooting
If you don’t see any data show up in the verification step, then check for these common problems.
Check Log4j:
- Wait a few minutes in case indexing needs to catch up
- Verify Log4j is working, such as by setting up a local file appender with the same format
- Run "sudo tcpdump -i lo -A udp and port 514" to verify UDP events are being sent to localhost
Check Your Syslog Daemon:
- Please check syslog file in /var/log/syslog if message not send to loggly.
- If log is getting truncated please check rsyslog.conf file and add $MaxMessageSize 64k if not exist.
- Troubleshooting Rsyslog
Still Not Working?
- Search or post your own questions on Java log4j and Apache log4j in the community forum.
The scripts are not supported under any SolarWinds support program or service. The scripts are provided AS IS without warranty of any kind. SolarWinds further disclaims all warranties including, without limitation, any implied warranties of merchantability or of fitness for a particular purpose. The risk arising out of the use or performance of the scripts and documentation stays with you. In no event shall SolarWinds or anyone else involved in the creation, production, or delivery of the scripts be liable for any damages whatsoever (including, without limitation, damages for loss of business profits, business interruption, loss of business information, or other pecuniary loss) arising out of the use of or inability to use the scripts or documentation.
