AppInsight for Active Directory requirements and permissions
Before using AppInsight for Active Directory, review the following requirements and recommendations.
| Requirements | |
|---|---|
| Host systems |
Configure systems as DCs running Active Directory (AD) Domain Services on a supported OS, including:
Only Microsoft DNS servers are currently supported. Add DCs to the SolarWinds Platform as monitored nodes.
|
| Permissions |
Provide domain credentials for an account that SAM can use to log in to AD to collect data.
Recommended: Use a dedicated AD account with limited permissions. See Set up AppInsight for Active Directory monitoring under the context of a "Least Privileges" account. |
| Ports |
The default ports for AppInsight for Active Directory appear below. To adjust port settings for individual domain controllers, see Configure AppInsight for Active Directory on nodes.
See also How AppInsight collects Active Directory data, below. |
| Encryption |
AD does not support encryption so the encryption method to connect to domain controllers is set to None, by default. To use SSL or StartTLS, add an LDAP certificate to the server manually. |
| Authentication |
By default, authentication is set to Negotiate so SAM can use Kerberos or NT LAN Manager (NTLM) authentication. |
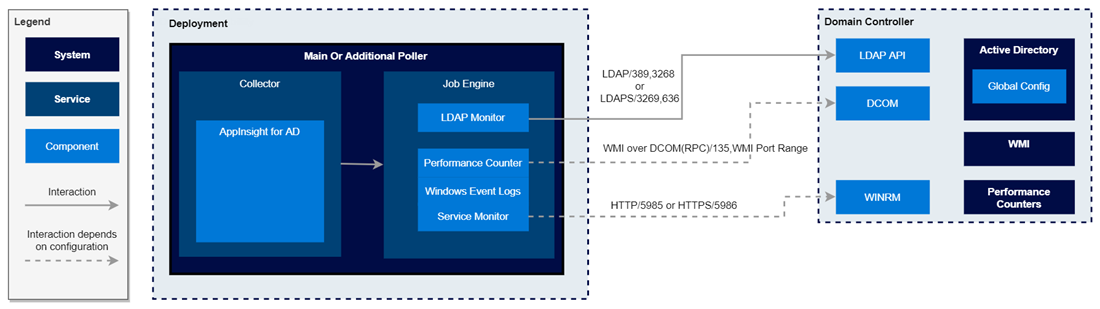
How AppInsight collects Active Directory data
In the AppInsight for Active Directory template, WinRM is the default transport method used to fetch data for WMI-based component monitors. If WinRM is disabled, WMI uses DCOM/RPC communication to allocate ports within the standard dynamic port range, 1025 — 65536. Enable the Inbound Rules in the WMI group and create firewall exceptions to allow TCP/UDP traffic on ports 1024 — 65535 so monitored objects that use WMI can be mapped.
- WMI TCP ports 1025 — 5000
- TCP ports 49152 — 65535
The following diagram shows how AppInsight uses various protocols to collect AD data: