OKTA SSO configuration and provisioning
On this page
Introduction
OKTA provides cloud software that helps companies manage and secure user authentication into modern applications, and helps developers to build identity controls into applications, website web services, and devices. For Service Desk), you can integrate Active Directory through OKTA.
You may connect simultaneously OKTA and Google.
Success of this setup depends on the parameter values that are customized for your organization. Use the Okta Administrator Dashboard to add an application and view the values that are specific to your needs.
Supported Features
The Okta/Service Desk SAML integration currently supports the following features:
- Service Provider (SP) -initiated SSO
- Identity Provider (IdPP) -initiated SSO
- JIT (Just In Time) Provisioning
For more information on the listed features, visit the Okta Glossary.
The instructions below cover all aspects of the configuration process.
Navigation
| ITSM customers | ESM customers |
|---|---|
| Setup > Account > Single Sign-On > Okta | Organization > Setup > Account > Single Sign-On > Okta |
Set up SSO and user provisioning with Okta
-
In Service Desk go to Setup > Account > Single Sign-On > Okta.
-
Identify your customer type below (single-tenant ITSM or ESM) and then perform the steps for that customer type:
-
Single-tenant customers need to perform the following steps:
For each of the Service Desk fields below, sign into the Okta Administrator Dashboard, and browse the App Catalog for Service Desk, then add the app. Copy/paste information from Okta into the appropriate field in Service Desk.In Okta In Service Desk Sign on URL Identity Provider URL Sign out URL Logout URL and Error URL Issuer SAML Issuer Signing Certificate Identity Provider x.509 Certificate -
ESM customers need to perform these steps instead of those above:
-
Sign in to the Okta Administrator Dashboard and browse the App Catalog for Service Desk, then add the app.
-
Open the General tab, go to SAML settings, and click Edit.
-
On the General Settings page, click Next.
-
On the Configure SAML page, edit the Single Sign-On URS and the Audience URI (SP Entity ID):
Edit the sub-domain by addingorg-before the account name. For example:From: https://account _name.samanage.com
To: https://org-account _name.samanage.com
-
Click Next and Finish to save your changes.
-
-
-
If you wish to enable Just In Time Provisioning, select the box labeled Create users if they do not exist.
-
If you plan to disable the current login option (username & password), check the box labeled Redirect to the SAML login page when logging into Service Desk by default.
Do not mark the box above until SAML configuration is tested successfully. After the box is checked, you will no longer be able to log in with your username/password. -
Click Update.
-
In Okta, select the Sign On tab for the Service Desk app, scroll down to the ADVANCED SIGN-ON SETTINGS section, and then click Edit.
-
Enter the ACS URL value into the corresponding field.
Make sure that you entered the correct value in the Subdomain field under the General application tab in Okta. Using the wrong value will prevent you from authenticating via SAML to Service Desk.If you have a custom Service Desk URL, obtain your ACS URL value as follows:
-
Go to
[customSolarWindsServiceDeskURL]/saml/metadata. An XML file like the following will display after the page loads: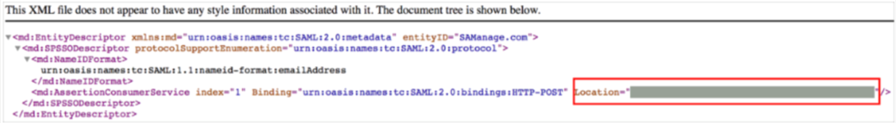
-
Locate and make a copy of your ACS URL value from the Location attribute.
-
-
Click Save.
There are different initial steps for single provider customers vs. ESM customers. The final steps should be completed by all customers.
Initial steps for single provider customers
- In Service Desk go to Setup > Account > Single Sign-On > Okta.
-
For each of the Service Desk fields below, sign into the Okta Administrator Dashboard to generate the variable, and copy/paste it into the appropriate field in Service Desk.
In Okta In Service Desk Sign on URL Identity Provider URL Sign out URL Logout URL and Error URL Issuer SAML Issuer Signing Certificate Identity Provider x.509 Certificate
Initial steps for ESM customers
-
Sign into the Okta Administrator Dashboard and select the Service Desk app.
-
Open the General tab, then go to SAML settings and click Edit.
-
At General Setting, no changes are required. Click Next.
-
At Configure SAML, edit the Single sign-on URL and Audience URI (SP Entity ID). Edit the sub-domain by adding “org-“ before the account name. For example:
-
From: https://account _name.samanage.com
-
To: https://org-account _name.samanage.com
-
-
Click Next, and then Finish to save your changes.
ESM Provisioning Step 1: Ensure provisioning at the organization level
Before you begin, determine whether your organization has already performed any provisioning.
-
For those who previously provisioned before migrating to ESM
Replace the token in the existing app with the token from the organization. Do not make any changes to the URL.
-
For those who have never provisioned
Provision users to the organization level. If your provisioning provider allows you to provision roles, you can also do that here.
-
Create a dedicated app in your provisioning provider platform.
-
Use the organization token for the provisioning process.
-
Use the organization URL.
-
ESM Provisioning Step 2: Provision at the service provider level
If you want service providers to be able to create roles and manage them at the service provider level, follow these steps:
-
Create a dedicated app in your provisioning provider platform.
-
Use the organization token for the provisioning process.
-
Use the specific service provider organization URL.
-
-
Repeat the role-provisioning process for any service provider that should be able to create and manage roles.
Final steps for all customers
-
If you plan to disable the current login option (username & password), check the box labeled Redirect to the SAML login page when logging into Service Desk by default.
DO NOT mark the box above until SAML configuration is tested successfully. After the box is checked, you will no longer be able to log in with your username/password. -
Click Update.
-
In Okta, select the Sign On tab for the Service Desk app, scroll down to the ADVANCED SIGN-ON SETTINGS section, and then click Edit.
-
Enter the ACS URL value into the corresponding field.
Make sure that you entered the correct value in the Subdomain field under the General application tab in Okta. Using the wrong value will prevent you from authenticating via SAML to Service Desk.If you have a custom Service Desk URL, obtain your ACS URL value as follows:
-
Go to
[customSolarWindsServiceDeskURL]/saml/metadata. An XML file like the following will display after the page loads:
-
Locate and make a copy of your ACS URL value from the Location attribute.
-
-
Click Save.
Log in with SP-initiated SSO
- Log in to the Service Desk URL and navigate to SSO.
- Click Single Sign-On.
