DPA 2024.2 release notes
Release date: April 17, 2024
These release notes were last updated on April 19, 2024
Here's what's new in Database Performance Analyzer 2024.2.
Learn more
- See the DPA 2024.2 system requirements.
- For information about working with DPA, see the DPA 2024.2 Administrator Guide.
New features and improvements in DPA
Security enhancements
The following drivers used by DPA have been upgraded to:
- Tomcat 9.0.85
- Open JDK 11.0.20.1 (Windows and Linux)
Table and index advisors for PostgreSQL
In addition to query advisors, DPA 2024.2 provides the following advisors for PostgreSQL database instances:
-
Table advisors are generated when a significant number of inefficient queries run against a table. Inefficient queries perform a large number of reads but return a small number of rows.
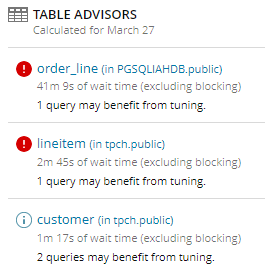
Click a table advisor to open the Table Tuning Advisor page, which displays aggregated information about the table, the inefficient queries that ran against it, and any existing indexes.
-
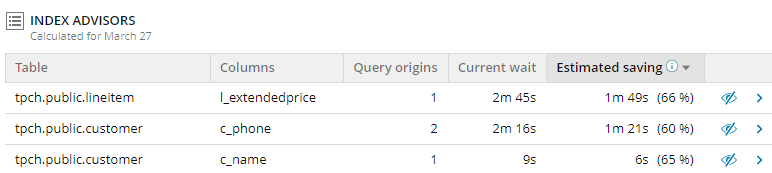
Index advisors identify missing indexes and provide estimates of how much time adding the suggested index could potentially save. You can view details or hide an advisor.
Information about top plans
To identify inefficient queries and analyze indexes, DPA must collect execution plans from PostgreSQL database instances. Plan information is available in the following places:
-
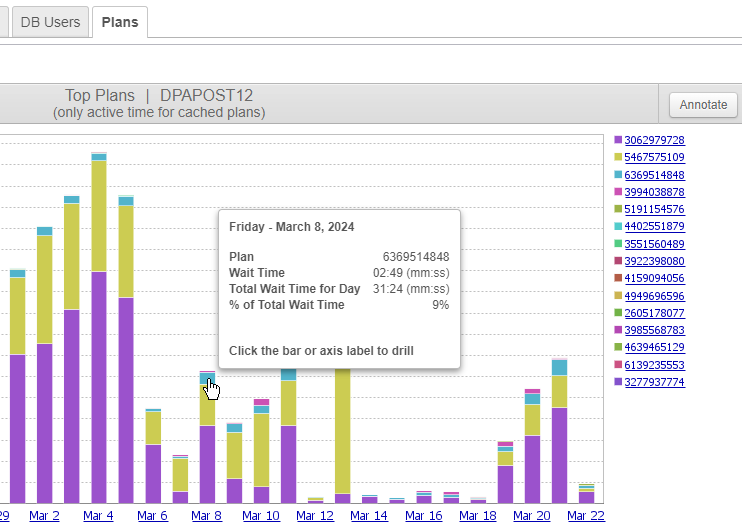
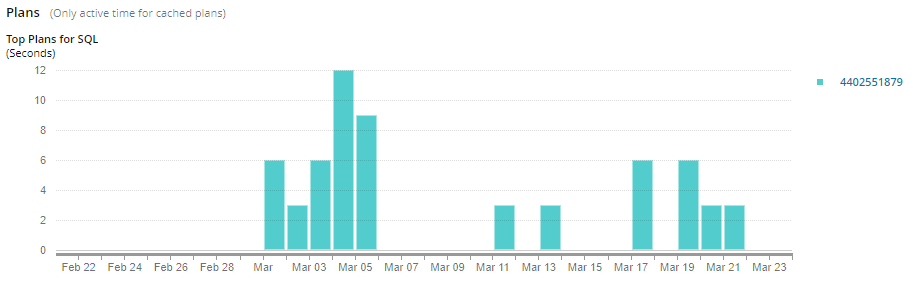
On the Trends tab, click the Plans tab to see a chart representing the cached plans with the highest wait times. Hover over part of a bar to see details about that plan.
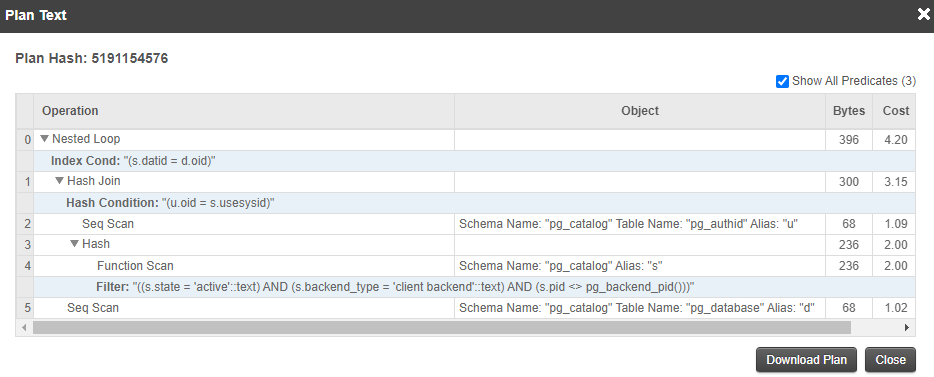
Click a plan hash in the legend to display the plan text. This helps you identify costly operations like sequential scans.
-
The Query Detail page displays wait times for plans associated with the selected query. As on the Trends tab, you can click a plan hash in the legend to display the plan text.
-
The Table Tuning Advisor page shows any inefficient steps in the plans for the inefficient queries that ran against the table. To display the plan text, click View plan details. For details and possible solutions, click the
 icon.
icon.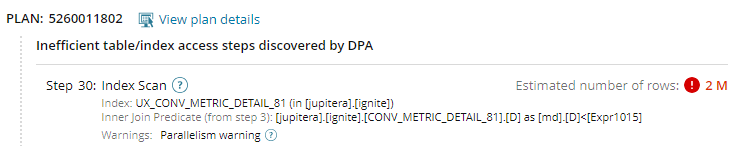
-
The following reports are now available for PostgreSQL database instances. They were previously available for Oracle and SQL Server database instances.
- Top Plans
- Top Plans for single SQL
- Top SQLs for single Plan
Requirements for upgrading customers
If you are monitoring PostgreSQL database instances with an earlier version of DPA, make the following changes to enable table and index advisors.
-
If the DPA monitoring user does not have the
SUPERUSERprivilege, grant the following additional privileges. These privileges enable the DPA monitoring user to collect execution plans, which it needs to generate index and table advisors.GRANT ALL ON ALL TABLES IN SCHEMA public TO dpa_user;At a minimum, the monitoring user must be granted
SELECT,INSERT,UPDATE, andDELETEprivileges. You can use a more granular command to list specific privileges and tables. Examples include:GRANT SELECT, INSERT, UPDATE, DELETE ON TABLE table_name TO dpa_user;GRANT SELECT, INSERT, UPDATE, DELETE ON ALL TABLES IN SCHEMA public TO dpa_user; -
DPA recommends increasing the
track_activity_query_sizevalue.PostgreSQL stores currently running SQL statements in the
pg_stat_activity.queryfield. If there is not enough memory allocated to store the entire SQL statement, it truncates the query. DPA cannot collect the execution plan for a truncated SQL statement. To avoid truncated queries, DPA recommends increasing the amount of reserved memory to 4096 bytes.-
For on-premises deployments, edit the
postgresql.conffile and modify the following entry:track_activity_query_size = 4096
-
For Amazon RDS deployments, use the AWS Console to modify your DB Parameter Group. Then change the
track_activity_query_sizeparameter value to4096. -
For Azure Single Server or Hyperscale deployments, modify your Server parameters to change ththe
track_activity_query_sizeparameter value to4096.
-
- Restart the PostgreSQL server.
-
Create the
pgstattupleextension in the database. This extension is database-bound and must be created for each database. It is required to enable DPA to display the Index Bloat Metrics percentage on a table advisor.To create the extension:
- Connect to the PostgreSQL database instance with the DPA user account or superuser (for EDB Enterprise edition).
-
Execute following command:
CREATE EXTENSION pgstattuple;
Alert information in DPA Central
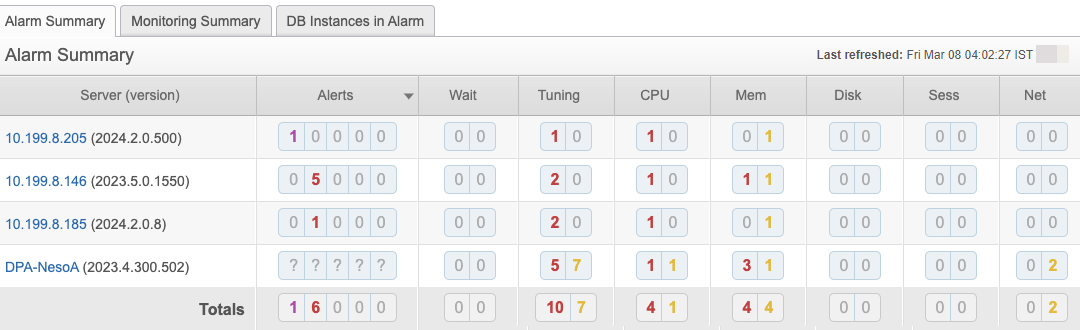
In addition to the information shown in previous DPA versions, the Alarm Summary tab on the Central page now shows:
- The number of broken alerts
- The number of alerts at each level that are triggered but not acknowledged
On the DB Instances in Alarm tab, the Alert column contains the broken alert icon ![]() if the instance has any broken alerts. Otherwise, it contains an icon to indicate the highest severity alert that is triggered but not acknowledged. When you sort by alarm severity and multiple rows have the same score, issues in the Alert column are given more weight than issues in other columns.
if the instance has any broken alerts. Otherwise, it contains an icon to indicate the highest severity alert that is triggered but not acknowledged. When you sort by alarm severity and multiple rows have the same score, issues in the Alert column are given more weight than issues in other columns.
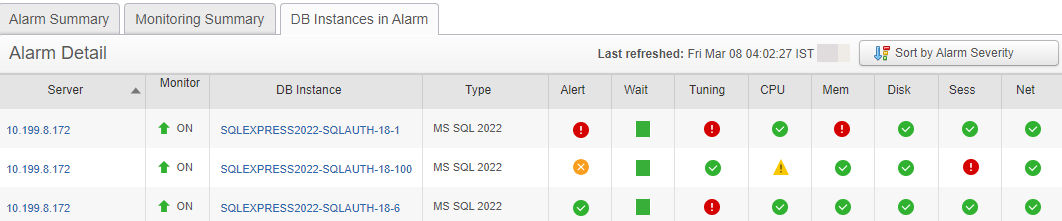
On both tabs, alert information is shown for DPA servers running DPA 2024.2 and later. For DPA servers running earlier versions, a question mark is displayed.
Microsoft Entra service principal authentication
When you register an Azure SQL Database instance or an Azure SQL Managed Instance (ASMI) for monitoring, you can choose to use a Microsoft Entra service principal (previously Azure service principle) for authenticating the monitoring user.
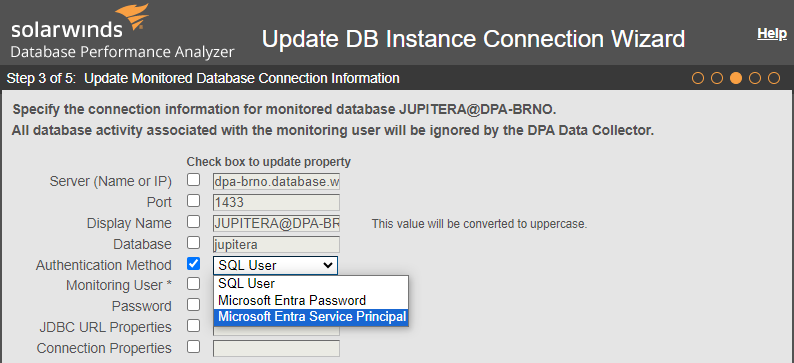
For Azure SQL Database and ASMI instances that are already registered, the Update DB Instance Connection Wizard includes a field to change the authentication method. You can change the authentication method between the following types:
- SQL User
- Microsoft Entra Password (formerly Azure Active Directory password)
- Microsoft Entra Service Principal (formerly Azure service principal)
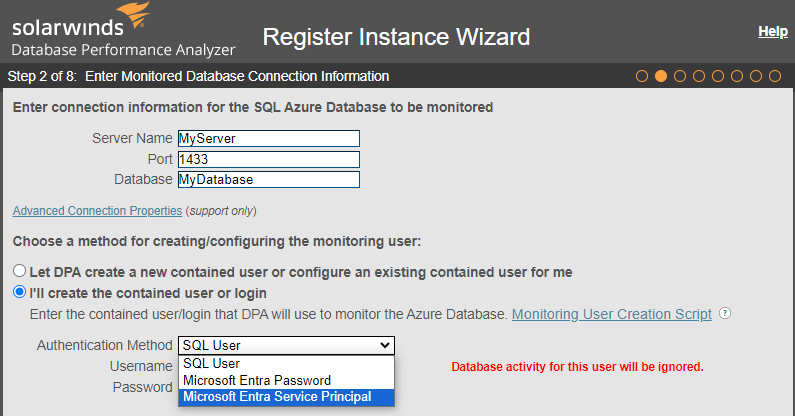
Option for specifying the authentication method for Azure SQL Database and ASMI instances
When you register an Azure SQL Database or ASMI instance, DPA 2024.2 provides the following options for specifying which authentication method is used. If the authentication method is not specified, password authentication is used.
Do not specify the authentication method in the Connection Properties field. Adding authentication information to that field will return an error.
If you installed a buddy drop that provided service principal authentication, the upgrader removes authentication information from the Connection Properties field and selects that option under Authentication method.
-
In the registration wizard, choose one of the following options under Authentication method:
SQL User– (Default) A SQL Server user passwordMicrosoft Entra Password– A Microsoft Entra (formerly Azure AD) passwordMicrosoft Entra Service Principal– A Microsoft Entra service principal (formerly Azure service principal)
-
In the mass registration spreadsheet, enter one of the following in the Authentication Method column:
PASSWORD– (Default) A SQL Server user passwordMEP– A Microsoft Entra (formerly Azure AD) passwordMESP– A Microsoft Entra service principal (formerly Azure service principal)
-
In a script to call the API, specify one of the following values for the authenticationSchema parameter:
PASSWORD– (Default) A SQL Server user passwordADorMEP– A Microsoft Entra (formerly Azure AD) passwordMESP– A Microsoft Entra service principal (formerly Azure service principal)
The value
ADwas introduced in a previous version. It is retained to maintain backward compatibility with existing scripts.
For detailed registration information, see the following topics:
- Register an Azure SQL Database
- Register an Azure SQL Managed Instance
- Register multiple database instances
Information about registering instances with the API is in Swagger. See Learn about and experiment with the DPA API for access information.
Port used to send data to the SolarWinds Platform
If you have configured the DPA Integration Module (DPAIM) on the SolarWinds Platform, DPA 2024.2 can use either port 17774 or 17778 to send data to the SolarWinds Platform. DPA now uses port 17774 by default, but you can set the system property com.confio.orion.hco.custom.port to define which port you want to use. To communicate, both DPA and the SolarWinds Platform must use the same port. For information about specifying which port they use, see Specify the port DPA uses....
Fixes
| Case number | Description |
|---|---|
| 01309215 |
Users can configure a company email server and DPA can authenticate to that server with any valid password. Some valid passwords no longer fail. |
| 01435343 |
Statistics (such as Executions, Rows Processed, Physical Reads, and Logical Reads) are available for all queries that run on Sybase monitored instances. Enabling statistics monitoring no longer returns the error |
| 01451096, 01460503, 01456415, 01457479, 01488113, 01518771, 01567625, 01568794 |
When you are monitoring a Db2 server with multiple databases, the following alerts now return data for all databases:
DPA 2024.2 also resolves other issues related to replacing the deprecated
|
| 01445160 |
The JDBC fetch size defines how many records are returned in one network call. If all data cannot be returned in one call because of the fetch size, multiple calls are issued. By default, PostgreSQL does not set a fetch size, and attempts to return all data in one call. When a large amount of data needed to be sent to DPA, DPA could run out of memory. When this occurred, the
In new installations of DPA 2024.2 and later, the
Upgrading customers, if you monitor PostgreSQL database instances, follow the instructions in DPA troubleshooting tips to add this property. |
| 01439523 |
UTL_CON is a package that DPA installs into the Any model changes made by the UTL_CON package is now logged in the wizard.log file. |
| 01539301 |
The default logging level for the following files associated with index analysis for Oracle has changed from WARN to TRACE:
This change prevents DPA logs from being filled with warnings such as the following when the index analysis job is unable to access a table (for example, because the table was deleted):
|
| 01466505 |
If licenses cannot be deactivated using the online method (for example because of a firewall), DPA opens a dialog that enables users to continue with offline deactivation. |
| 01522316 |
The Ineffective Statistics alert for SQL Server, Azure SQL Server Managed Instance, and Azure SQL Database instances is no longer triggered by data in system tables. |
Third-party CVEs
SolarWinds would like to thank our Security Researchers below for reporting on the issue in a responsible manner and working with our security, product, and engineering teams to fix the vulnerability.
| CVE-ID | Vulnerability Title | Description | Severity |
|---|---|---|---|
| CVE-2023-46589 | Tomcat Improper Input Validation Vulnerability | Tomcat did not correctly parse HTTP trailer headers. A specially crafted trailer header that exceeded the header size limit could cause Tomcat to treat a single request as multiple requests leading to the possibility of request smuggling when behind a reverse proxy. | 7.5 (HIGH) |
| CVE-2023-21843 | Vulnerability in the Oracle Java SE, Oracle GraalVM Enterprise Edition | This vulnerability allows unauthenticated attacker with network access via multiple protocols to compromise Oracle Java SE, Oracle GraalVM Enterprise Edition. Successful attacks of this vulnerability can result in unauthorized update, insert or delete access to some of Oracle Java SE, Oracle GraalVM Enterprise Edition accessible data. | |
| CVE-2023-21835 | Vulnerability in the Oracle Java SE, Oracle GraalVM Enterprise Edition product | This vulnerability allows unauthenticated attacker with network access via DTLS to compromise Oracle Java SE, Oracle GraalVM Enterprise Edition. Successful attacks of this vulnerability can result in unauthorized ability to cause a partial denial of service (partial DOS) of Oracle Java SE, Oracle GraalVM Enterprise Edition. | |
| CVE-2023-21830 | Vulnerability in the Oracle Java SE, Oracle GraalVM Enterprise Edition | This vulnerability allows unauthenticated attacker with network access via multiple protocols to compromise Oracle Java SE, Oracle GraalVM Enterprise Edition. Successful attacks of this vulnerability can result in unauthorized update, insert or delete access to some of Oracle Java SE, Oracle GraalVM. |
Before you upgrade!
As a result of the changes made to correct issues with monitoring Db2 database instances, upgrading customers monitoring Db2 instances need to grant an additional privilege to the DBA monitoring user. Run this command on each Db2 instance, changing userName to the monitoring user:
grant execute on function SYSPROC.MON_GET_MEMORY_POOL to userName;
This change can be made before or after the upgrade, but to ensure continuous monitoring, SolarWinds recommends that you make it before the upgrade.
Installation or upgrade
For new installations, you can download the installer from the SolarWinds website or from the Customer Portal. For more information, see the DPA Installation and Upgrade Guide.
For upgrades, use the DPA Installation and Upgrade Guide to help you plan and execute your upgrade. When you are ready, download the upgrade package from the SolarWinds Customer Portal.
Known issues
Custom alerts and custom metrics are not supported on a Db2 server with multiple databases
When you are monitoring a Db2 server with multiple databases, custom alerts and custom metrics do not return data for all databases. Because of a limitation with MON_GET_* functions, custom alerts and custom metrics are supported only for connected databases.
Resolution or Workaround: None.
Mass registration for Azure SQL Database instances
The script to generate the mass registration file for an Azure SQL Database instance has not yet been updated to reflect the changes to mass registration fields. DPA 2024.2 cannot use the file created by this script.
Resolution or workaround: Use the wizard or the API to register Azure SQL Database instances.
DPA does not always use the Microsoft JDBC driver by default
When you register a database instance for monitoring, DPA should use the Microsoft JDBC driver by default. However, it uses the jTDS JDBC driver by default if the system.properties file does not contain the following entry:
com.confio.ignite.jdbc.sqlserver.useJtdsDriver=false
This missing configuration is likely to happen on DPA servers where older versions of DPA were initially installed, before DPA began using the Microsoft Driver.
Resolution or Workaround:
Open the system.properties file in a text editor, and determine if it contains the entry above. If not, manually add it and save the file.
PostgreSQL OS CPU utilization not showing data on a Windows installation
When PostgreSQL is installed on a server with a Windows operating system, the O/S CPU Utilization resource metric in DPA does not display any data. It displays the message Chart doesn't have data collected for selected time period.
If PostgreSQL OS CPU utilization data is missing in other environments, make sure the system_stats extension is installed. For instructions, see Register a PostgreSQL database instance and prepare for monitoring.
Resolution or Workaround: None.
Importing an alert definition without the associated database assignment rule
In some situations, the log file shows the status of an imported alert definition as both Imported and Failed. This occurs when the alert definition uses a database assignment rule, but the rule was not imported and did not already exist on the server.
The two statuses indicate that the alert definition was imported, but the attempt to associate the database assignment rule failed.
Resolution or Workaround: When you import an alert definition that uses a database assignment rule, either import the rule or ensure that it already exists on the server.
If you imported an alert definition and the associated rule is missing, you must edit the alert definition to specify the database instances. (You can specify instances by manually selecting them or by applying a rule.)
End of life
| Version | EoL Announcement | EoE Effective Date | EoL Effective Date |
|---|---|---|---|
| DPA 2023.1 |
April 19, 2024 End-of-Life (EoL) announcement - Customers on DPA version 2023.1 or earlier should begin transitioning to the latest version of DPA. |
May 20, 2024 End-of-Engineering (EoE) - Service releases, bug fixes, workarounds, and service packs for DPA version 2023.1 or earlier will no longer actively be supported by SolarWinds. | May 19, 2025 End-of-Life (EoL) - SolarWinds will no longer provide technical support for DPA version 2023.1 or earlier. |
| DPA 2022.4 |
January 19, 2024 End-of-Life (EoL) announcement - Customers on DPA version 2022.4 or earlier should begin transitioning to the latest version of DPA. |
May 20, 2024 End-of-Engineering (EoE) - Service releases, bug fixes, workarounds, and service packs for DPA version 2022.3 or earlier will no longer actively be supported by SolarWinds. | May 19, 2025 End-of-Life (EoL) - SolarWinds will no longer provide technical support for DPA version 2022.3 or earlier. |
| DPA 2022.3 |
November 23, 2023 End-of-Life (EoL) announcement - Customers on DPA version 2022.3 or earlier should begin transitioning to the latest version of DPA. |
April 12, 2024 End-of-Engineering (EoE) - Service releases, bug fixes, workarounds, and service packs for DPA version 2022.3 or earlier will no longer actively be supported by SolarWinds. | April 14, 2025 End-of-Life (EoL) - SolarWinds will no longer provide technical support for DPA version 2022.3 or earlier. |
| DPA 2022.2 |
April 18, 2023 End-of-Life (EoL) announcement - Customers on DPA version 2022.2 or earlier should begin transitioning to the latest version of DPA. |
August 18, 2023 End-of-Engineering (EoE) - Service releases, bug fixes, workarounds, and service packs for DPA version 2022.2 or earlier will no longer actively be supported by SolarWinds. | April 18, 2024 End-of-Life (EoL) - SolarWinds will no longer provide technical support for DPA version 2022.2 or earlier. |
| DPA 2022.1 |
January 18, 2023 End-of-Life (EoL) announcement - Customers on DPA version 2022.1 or earlier should begin transitioning to the latest version of DPA. |
April 18, 2023 End-of-Engineering (EoE) - Service releases, bug fixes, workarounds, and service packs for DPA version 2022.1 or earlier will no longer actively be supported by SolarWinds. | April 18, 2024 End-of-Life (EoL) - SolarWinds will no longer provide technical support for DPA version 2022.1 or earlier. |
See the End of Life Policy for information about SolarWinds product life cycle phases. To see EoL dates for earlier DPA versions, see DPA release history.
End of support
Monitored database versions
Database Performance Analyzer 2024.2 no longer supports monitoring the following database versions. These versions are currently unsupported by the vendor.
Self-managed
- MariaDB 10.2
- MariaDB 10.1
- MariaDB 10.0
- MySQL 5.7
- MySQL 5.6.10
- Oracle 18.4
- Oracle 12.2
- Oracle 12.1
- Oracle 11.2
- Percona 5.7
- Percona 5.6
- PostgreSQL 11
- PostgreSQL 10
- PostgreSQL 9.6
- EDB Postgres 11
- EDB Postgres 10
- EDB Postgres 9.6
- SQL Server 2017
- SQL Server 2016
- SQL Server 2014
- SQL Server 2012
- Sybase (SAP ASE) 15.7
- Sybase (SAP ASE) 15.5
Amazon RDS
- Amazon RDS for MySQL 5.7
- Amazon RDS for MySQL 5.6.10
- Amazon RDS for SQL Server 2017
- Amazon RDS for SQL Server 2016
- Amazon RDS for SQL Server 2014
- Amazon RDS for PostgreSQL 11
- Amazon RDS for PostgreSQL 10
- Amazon RDS for PostgreSQL 9.6
- Amazon RDS for PostgreSQL EDB 11
- Amazon RDS for PostgreSQL EDB 10
- Amazon RDS for PostgreSQL EDB 9.6
Amazon Aurora
- Amazon Aurora for MySQL-compatible 5.7
- Amazon Aurora for MySQL-compatible 5.6
- Amazon Aurora for PostgreSQL-compatible 11
- Amazon Aurora for PostgreSQL-compatible 10
- Amazon Aurora for PostgreSQL-compatible 9.6
Microsoft Azure
- Azure Database for PostgreSQL - Single Server 11
- Azure Database for PostgreSQL - Single Server 10
- Azure Database for PostgreSQL - Single Server 9.6
- Azure Database for PostgreSQL - Flexible Server 11
- Azure Database for MySQL - Single Server 5.7
- Azure Database for MariaDB 10.2
Google Cloud SQL
- Cloud SQL for MySQL 5.7
- Cloud SQL for PostgreSQL 11
- Cloud SQL for PostgreSQL 10
- Cloud SQL for PostgreSQL 9.6
DPA repository database versions
Database Performance Analyzer 2024.2 no longer supports using the following database versions as the DPA repository database. These versions are currently unsupported by the vendor.
Self-managed
- MySQL 5.7
- MySQL 5.6
- Oracle 18.4
- Oracle 12.2
- Oracle 12.1
- SQL Server 2017
- SQL Server 2016
- SQL Server 2014
Amazon RDS
- Amazon RDS for MySQL 5.7
- Amazon RDS for MySQL 5.6
Amazon Aurora
- Amazon Aurora for MySQL-compatible 5.7
- Amazon Aurora for MySQL-compatible 5.6
Legal notices
© 2024 SolarWinds Worldwide, LLC. All rights reserved.
This document may not be reproduced by any means nor modified, decompiled, disassembled, published or distributed, in whole or in part, or translated to any electronic medium or other means without the prior written consent of SolarWinds. All right, title, and interest in and to the software, services, and documentation are and shall remain the exclusive property of SolarWinds, its affiliates, and/or its respective licensors.
SOLARWINDS DISCLAIMS ALL WARRANTIES, CONDITIONS, OR OTHER TERMS, EXPRESS OR IMPLIED, STATUTORY OR OTHERWISE, ON THE DOCUMENTATION, INCLUDING WITHOUT LIMITATION NONINFRINGEMENT, ACCURACY, COMPLETENESS, OR USEFULNESS OF ANY INFORMATION CONTAINED HEREIN. IN NO EVENT SHALL SOLARWINDS, ITS SUPPLIERS, NOR ITS LICENSORS BE LIABLE FOR ANY DAMAGES, WHETHER ARISING IN TORT, CONTRACT OR ANY OTHER LEGAL THEORY, EVEN IF SOLARWINDS HAS BEEN ADVISED OF THE POSSIBILITY OF SUCH DAMAGES.
The SolarWinds, SolarWinds & Design, Orion, and THWACK trademarks are the exclusive property of SolarWinds Worldwide, LLC or its affiliates, are registered with the U.S. Patent and Trademark Office, and may be registered or pending registration in other countries. All other SolarWinds trademarks, service marks, and logos may be common law marks or are registered or pending registration. All other trademarks mentioned herein are used for identification purposes only and are trademarks of (and may be registered trademarks) of their respective companies.
