Error code 16022 HTTPS listener exists on port 5986
Error: An HTTPS listener currently exists on port 5986.
Cause: This error means that an HTTPS listener already exists on port 5986 and cannot be reused because it is not configured to listen for the target IIS server IP address.
Resolution: For details, see the log on the target computer located at: [ALLUSERSPROFILE]\ProgramData\Solarwinds\Logs\APM\RemoteIISConfigurator.log and RemoteIISConfiguratorPowerShell.log. For configuring WinRM using a different port, complete the following steps. When complete, rerun the steps in Assign AppInsight for IIS to nodes in SAM.
Configure WinRM on a server:
Important: To configure the listener, change 5986 to an available port number throughout these steps.
- Open a command prompt with the option Run as Administrator.
- Type:
winrm create winrm/config/listener?Address=*+Transport=HTTPS @{Port="5986";CertificateThumbprint="<Thumbprint value of certificate>";Hostname="<IP Address of Server>_Solarwinds_IIS_Zero_Configuration"}and press Enter.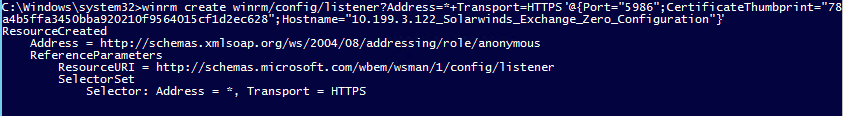
-
Verify the configuration by typing the following:
winrm get winrm/config/listener?Address=*+Transport=HTTPS.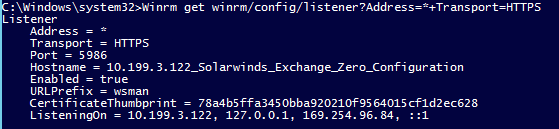
Next, create a firewall rule:
- Open PowerShell in the Run as Administrator context.
- Create a function for adding firewall rules using the following code:
function Add-FirewallRule { param( $name, $tcpPorts, $appName = $null, $serviceName = $null ) $fw = New-Object -ComObject hnetcfg.fwpolicy2 $rule = New-Object -ComObject HNetCfg.FWRule $rule.Name = $name if ($appName -ne $null) { $rule.ApplicationName = $appName } if ($serviceName -ne $null) { $rule.serviceName = $serviceName } $rule.Protocol = 6 #NET_FW_IP_PROTOCOL_TCP $rule.LocalPorts = $tcpPorts $rule.Enabled = $true $rule.Grouping = "@firewallapi.dll,-23255" $rule.Profiles = 7 # all $rule.Action = 1 # NET_FW_ACTION_ALLOW $rule.EdgeTraversal = $false $fw.Rules.Add($rule) } - Run the function to create the firewall exception for WSMAN using the following command:
Add-FirewallRule "Windows Remote Management" "5986" $null $null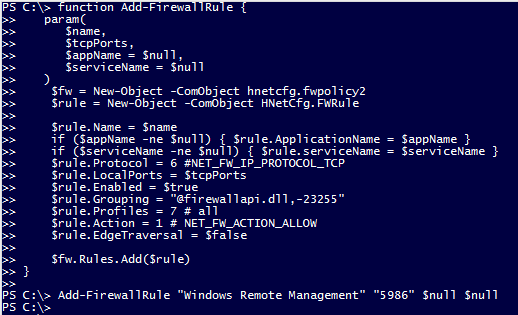
- Verify the rule was created by navigating to Control Panel > Windows Firewall > Advanced Settings.
