Configure audit policies for the domain controllers (DC)
To access AD Logga functionality you must activate specific audit policies.
If you want to make changes to audit policy you must be a member of the appropriate domain admin or organization admin group.
Configure audit policies for DCs on Server 2008
Before configuring audit policies you can verify if all required categories may already be activated.
You can enable the required audit policies by running the following commands on every DC with admin rights:
Monitor policy changes
auditpol /set /subcategory:{0CCE922F-69AE-11D9-BED3-505054503030} /success:enable
Directory service changes
auditpol /set /subcategory:{0CCE923C-69AE-11D9-BED3-505054503030} /success:enable
Managing User Accounts
auditpol /set /subcategory:{0CCE9235-69AE-11D9-BED3-505054503030} /success:enable
Managing computer accounts
auditpol /set /subcategory:{0CCE9236-69AE-11D9-BED3-505054503030} /success:enable
Managing security groups
auditpol /set /subcategory:{0CCE9237-69AE-11D9-BED3-505054503030} /success:enable
Managing distribution groups
auditpol /set /subcategory:{0CCE9238-69AE-11D9-BED3-505054503030} /success:enable
Managing application groups
auditpol /set /subcategory:{0CCE9239-69AE-11D9-BED3-505054503030} /success:enable
Other account management events
auditpol /set /subcategory:{0CCE923A-69AE-11D9-BED3-505054503030} /success:enable
Repeat this process for every DC!
Configure audit policies for DCs on Server 2008 R2 or higher
You can use the group policy editor to manage audit policy on server 2008 R2 or higher. This means you only need to implement the policy once rather than having to repeat it for every DC.
Please note that the activation of audit policy may be delayed on the domain controllers (DCs) depending on your replication interval.
Once you have completed these settings:
- complete a manual policy update with the command "
gpupdate /force" - Verify the audit policies settings
Screenshots property of © 2020 Microsoft.
Start managing group policies, by opening:
gpmc.msc
Screenshots property of © 2020 Microsoft.
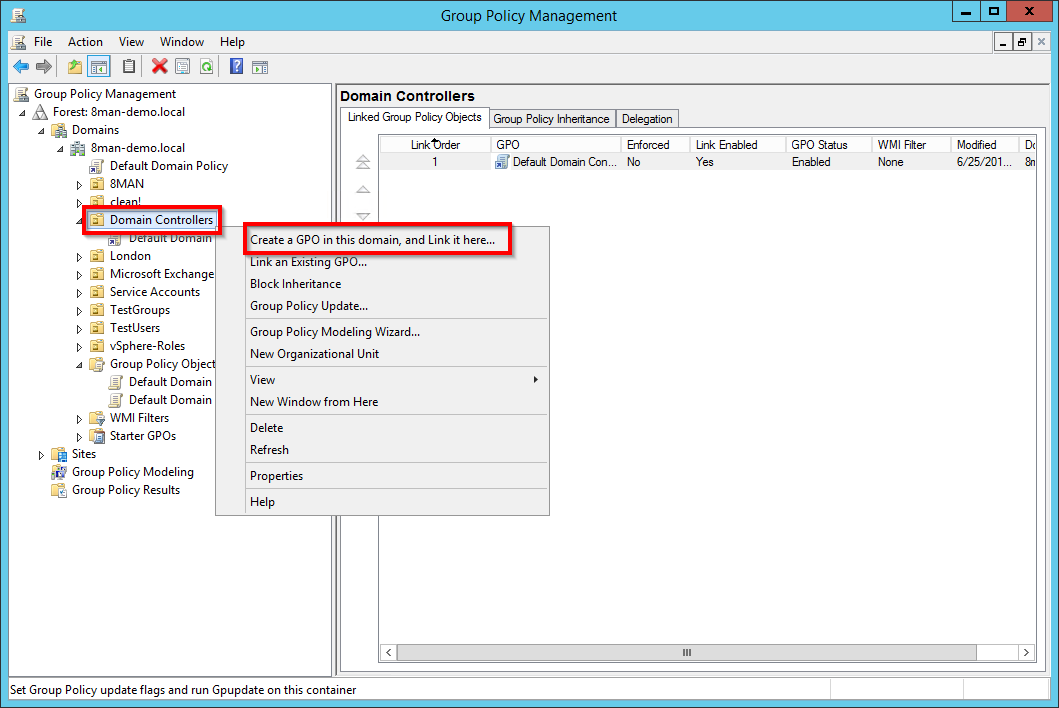
Create a new group policy.
Select the OU in which the DC computer accounts are located. By default they are located in the OU "Domain Controllers".
Ensure that the newly created policy is applied/winning to the appropriate DCs (hierarchy and order).
The order in which you set the options affects the effectiveness of the policy. Follow the order given here!
Screenshots property of © 2020 Microsoft.
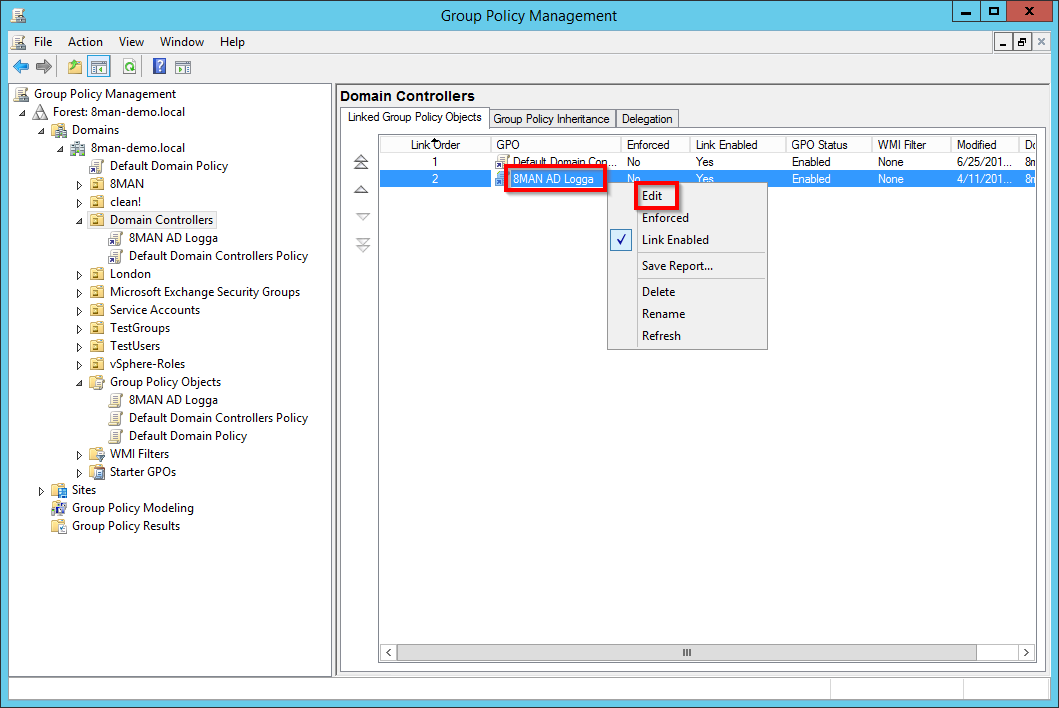
Select the newly created group policy by right clicking and selecting "edit".
Screenshots property of © 2020 Microsoft.
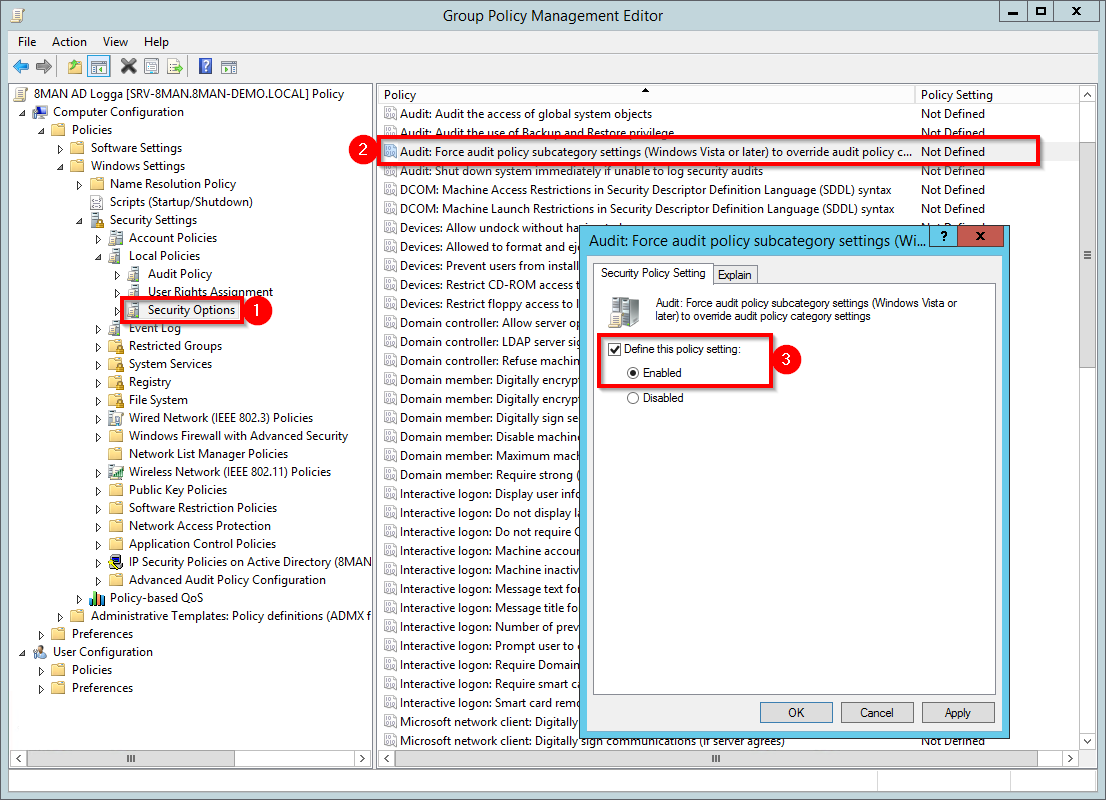
- Navigate to "security options".
- Double-click the policy "Audit: Force audit policy...".
- Activate the security policy as shown in the screenshot.
The order in which you set the options affects the effectiveness of the policy. Follow the order given here!
Screenshots property of © 2020 Microsoft.
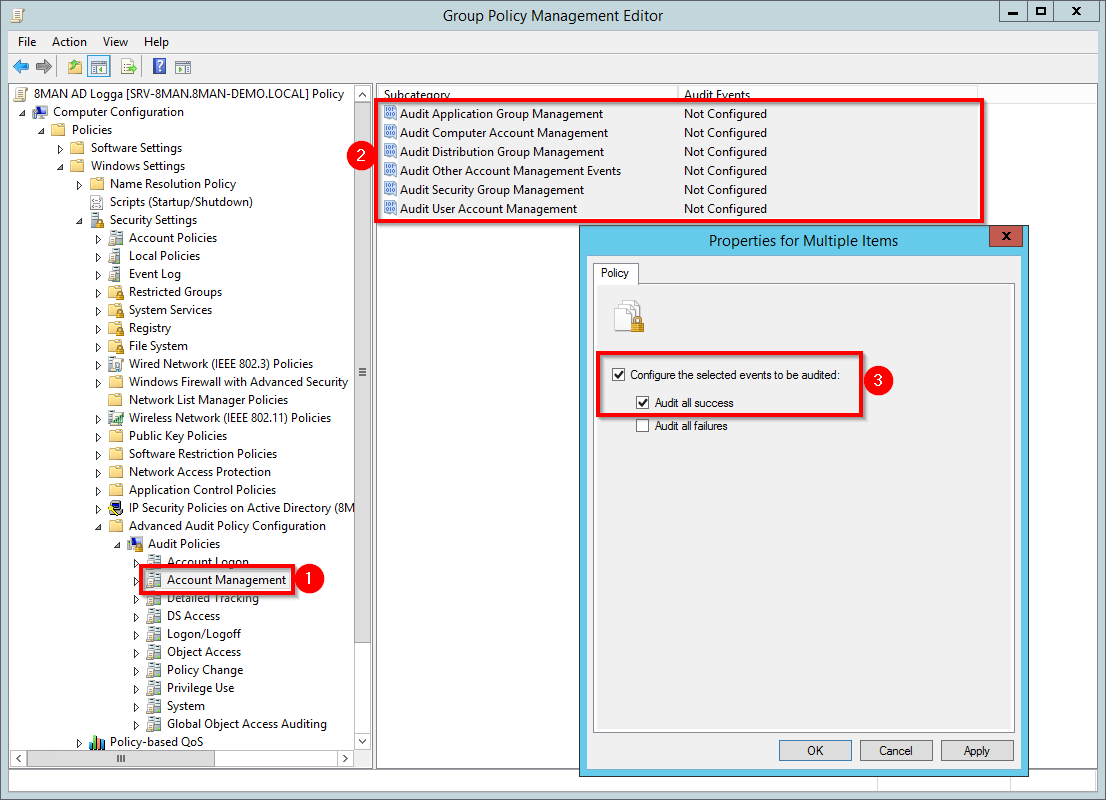
- Navigate to account management.
- Use multi-select and select all subcategories.
- Activate the audit by right-clicking and selecting "Properties", as shown in the diagram.
Screenshots property of © 2020 Microsoft.
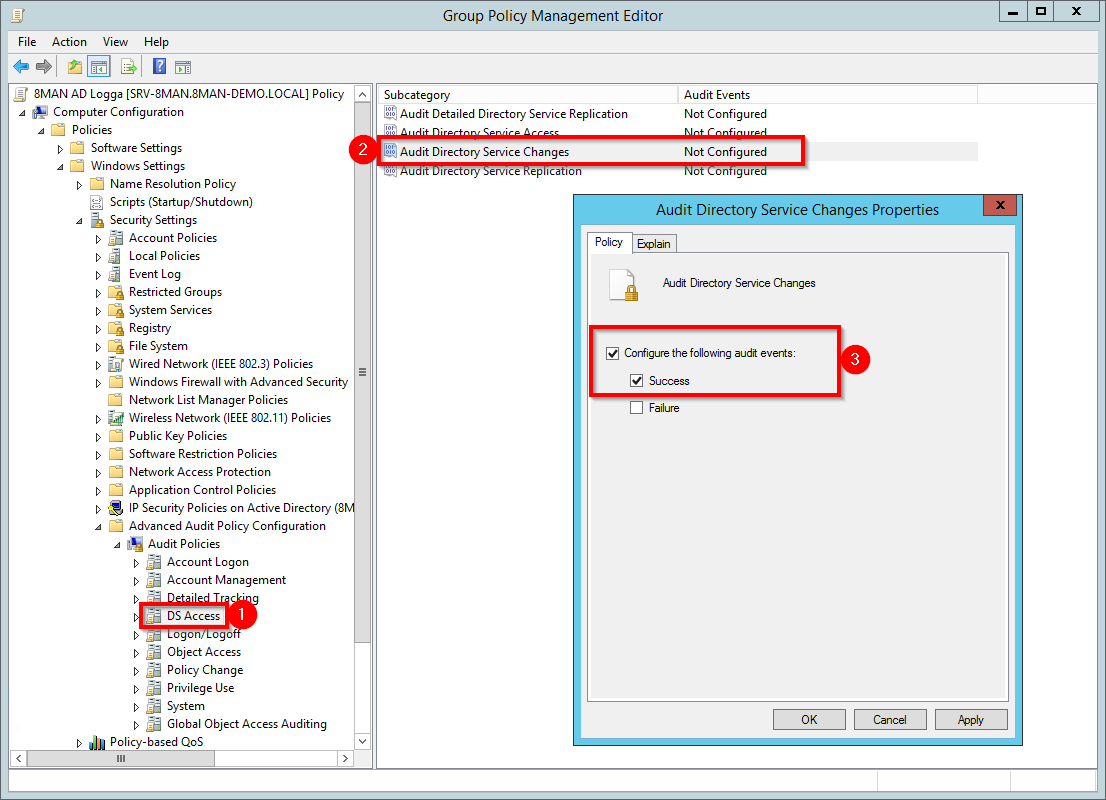
- Navigate to "DS Access".
- Double-click the subcategory "Audit Directory Service Changes".
- Activate the audit as shown in the screenshot.
Screenshots property of © 2020 Microsoft.
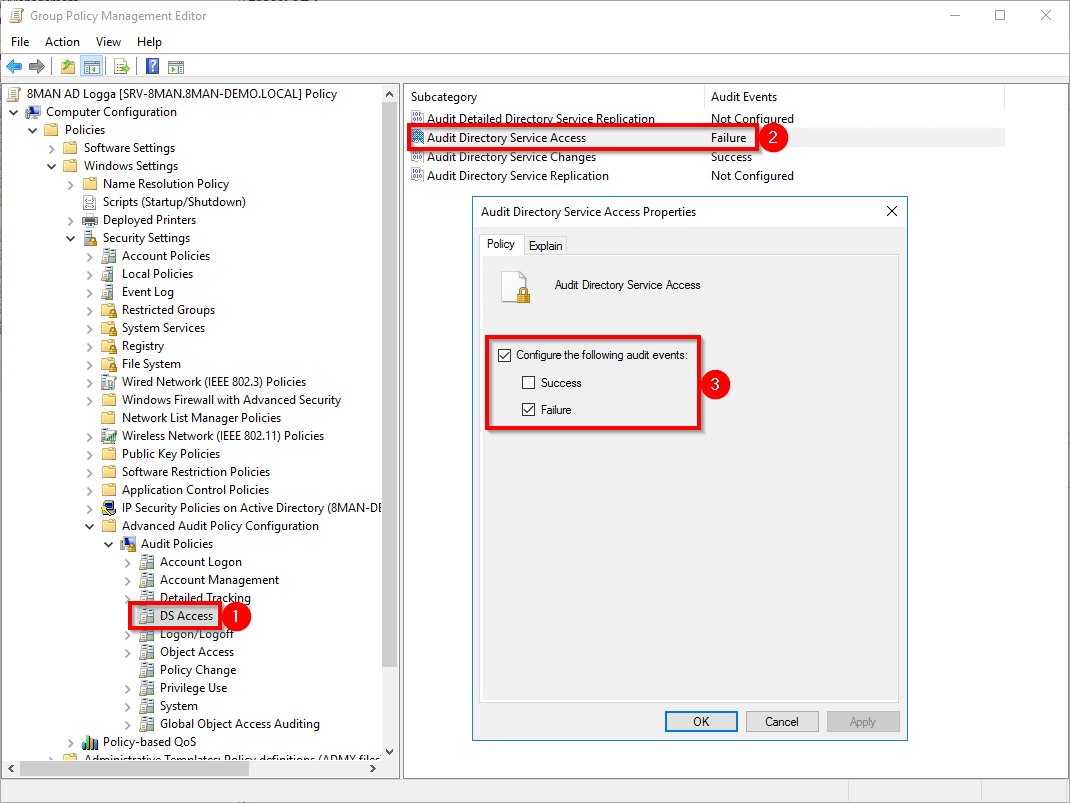
- Navigate to "DS Access".
- Double-click the subcategory "Audit Directory Service Access".
- Activate the audit in case of failure, as shown in the screenshot.
Screenshots property of © 2020 Microsoft.
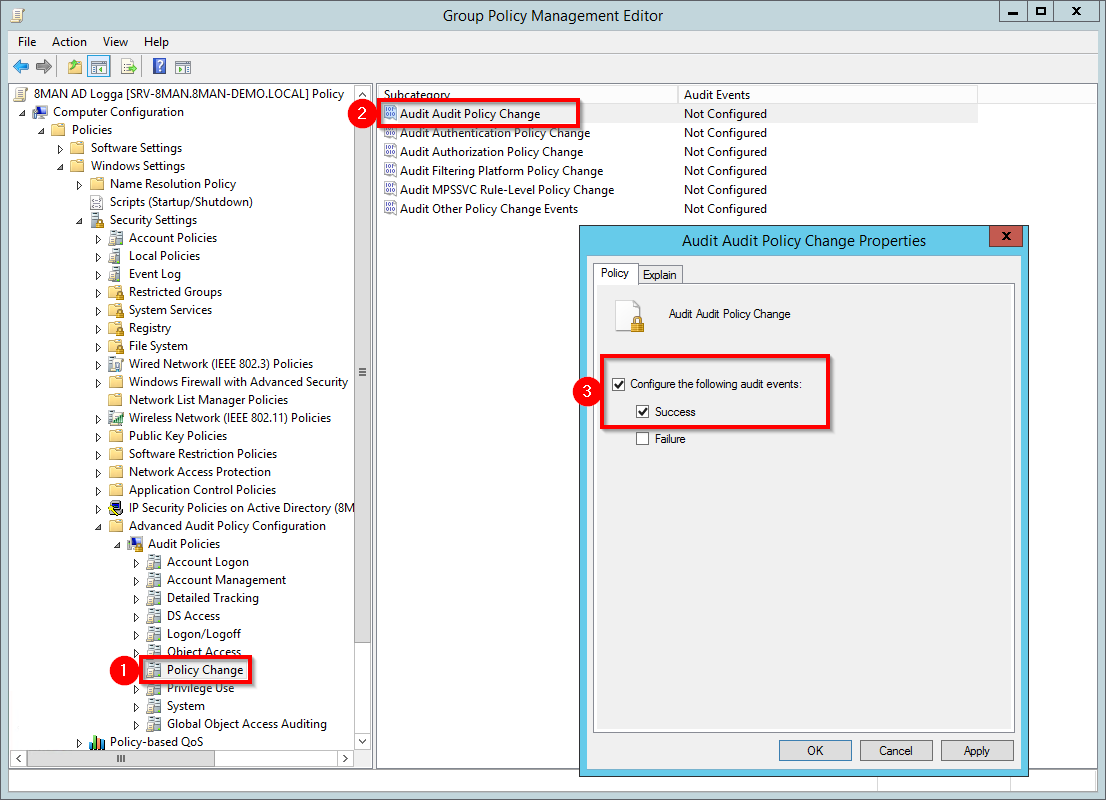
- Navigate to "Policy Change".
- Double-click the subcategory "Audit Audit Policy Change".
- Activate the audit as shown in the screenshot.
Once you have completed these settings:
- complete a manual policy update with the command "
gpupdate /force" - Verify the audit policies settings
Configure the AD Logga disk space requirement
1000 events require approximately 0.57 MB of storage in the data base.
By default the storage period of AD Logga events is set to 30 days and can be managed under server -> storage of scans.
Set the size of the Windows event log
To ensure that you don't "lose" any events, you must configure the maximum size for security event logs appropriately. For audit policy settings the storage requirements is roughly 1KB per event.
For example:
For a server outage or maintenance time (of the collector server selected for the AD Logga) of one hour, with approximately 1000 events per hour, the absolute minimum security event log size would be 1MB. Considering the low storage space requirements for 1000 events, the uncertainty of outage times as well as the potential relevance of individual security events we highly recommend that you ensure that enough storage space is available.
For more information about recovery mode, see the article Set Maximum Log Size. (© 2020 Microsoft, https://docs.microsoft.com/en-us/previous-versions/windows/it-pro/windows-server-2008-R2-and-2008/cc748849(v=ws.11), obtained on January 29, 2020)
Verify the audit policy settings
You can verify the effectiveness of audit policies by starting the command prompt with admin rights and entering the following command:
For english servers
auditpol /get /category:"policy change,account management,ds access"For all languages
auditpol /get /category:*
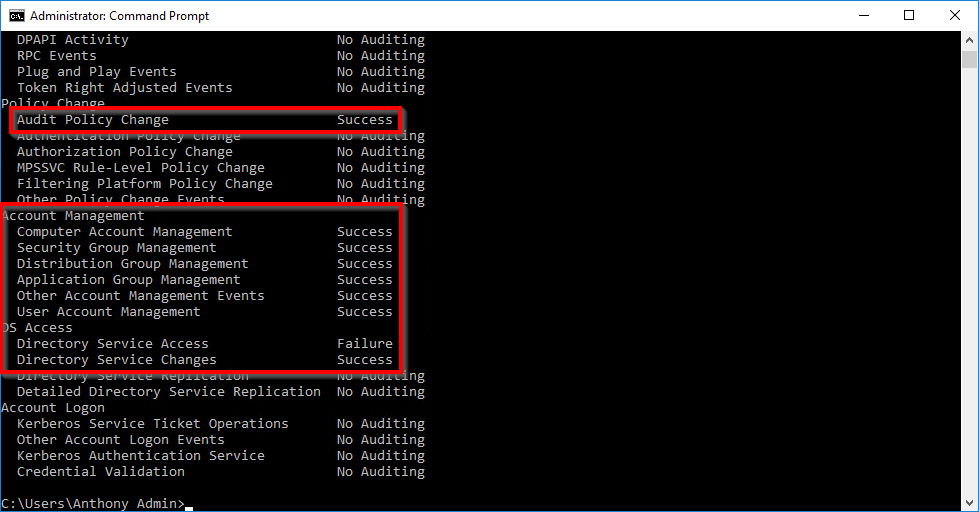
Screenshots property of © 2020 Microsoft.
The marked subcategories must be set to "Success" or "Failure" as shown.
