Configure the group policy to enable third-party updates
Perform this procedure only if your organization implements a group policy on all corporate systems.
The group policy defines the user, security, and networking policies for all computers in the network. To enable the managed computers to receive third-party updates from the WSUS server, export the software publishing certificate from the WSUS server to a certificate file. When you are finished, configure the Group Policy Object (GPO) on the domain controller and import the certificate file and the supporting Windows® Update policies.
Patch Manager signs all third-party packages with the software publishing certificate. This certificate must be installed in the local Trusted Root Certification Authority and Trusted Publishers keystores of each managed computer so they can receive third-party updates.
Export the software publishing certificate from the WSUS server
Export the software publishing certificate so you can add the file to the Group Policy (GPO). When you push the GPO to the managed systems, each system can accept third-party updates from non-Microsoft® sources.
-
Select the WSUS server in the Patch Manager menu.
- In the Actions column, click Software Publishing Certificate.
-
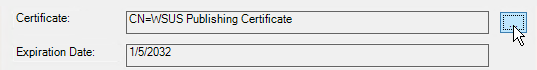
Click [...] in the Publishing Certificate Information window.
-
On the Details tab, select the WSUS publishing certificate.
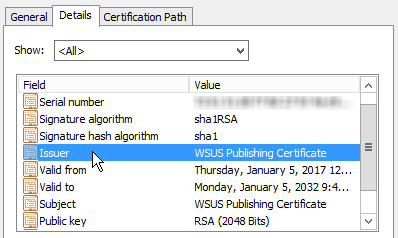
- Click Copy to File in the Certificate window.
- Click Next in the Certificate Export Wizard.
- Select DER encoded binary X.509 (.CER), and click Next.
- Enter a file name (for example,
WSUS Publishing Certificate). -
Complete the Certificate Export Wizard.
The software publishing certificate is exported to a file.
Configure the GPO for the targeted domain
This procedure configures Windows Update policies to the certificate stores on the managed computers so they accept third-party updates from non-Microsoft sources.
- Log in to the domain controller as an administrator.
- Copy the software publishing certificate to the domain controller desktop or another location on the server.
- Navigate to the control panel and open Group Policy Management.
-
In the Group Policy Management menu, navigate to the domain that contains the GPO for the targeted domain (for example,
Default Domain Policy).
If you need to create a GPO, right-click the domain (for example,
gir.lab), select Create a GPO in this domain, and link it here. Enter a name for the GPO, and click OK. The domain tree displays the GPO. -
Double-click the GPO (for example,
Default Domain Policy). -
Review the Group Policy Management Console window text, and click OK.
The Scope tab is displayed.
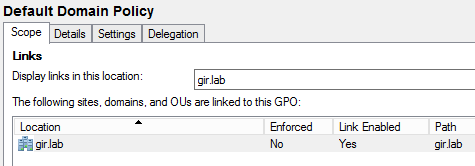
-
In the Windows Update window, enable:
Allow signed updates from an intranet Microsoft update service locationThis setting enables Windows Update on managed computers to accept non-Microsoft updates (or third-party updates) from a Microsoft Update location (or WSUS server) in the corporate network.
- Right-click the GPO and select Edit.
- In the Group Policy Management Editor, expand Computer Configuration > Policies > Administrative Templates > Windows Components.
- Scroll down and select Windows Update.
- Double-click Allow signed updates from an intranet Microsoft update service location in the Windows Update window.
- Select Enabled in the Configure Automatic Updates window.
-
Click OK.
This policy setting is displayed as Enabled in the Windows Update window.
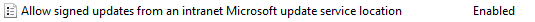
-
Add the WSUS software publishing certificate to the group policy.
This process adds the publishing certificate to the Trusted Root Certification Authority and Trusted Publishers certificate stores in the managed computers, enabling each computer to establish a secure network connection to the WSUS server and receive third-party updates.
- In the Group Policy Management Editor, click Policies > Windows Settings > Security Settings > Public Key Policies > Trusted Root Certification Authorities.
- Right-click Trusted Root Certification Authorities and select Import.
-
Complete the Certificate Import Wizard.
When you are finished, the WSUS certificate is imported into the Trusted Root Certification Authority directory. This directory includes SolarWinds certificates, Microsoft certificates, and all certificates in the Third-Party Root Certification Authorities keystore.
- Navigate to the Public Key Policies directory.
- Expand the directory, right-click Trusted Publishers, and select Import.
-
Complete the Certificate Import wizard.
When you are finished, the certificate is imported into the Trusted Publishers directory. This directory includes certificates from trusted Certificate Authorities.
The WSUS software publishing certificate is added to the group policy.
- Enable and configure the Configure Automatic Updates policy setting so the managed computers can automatically check the WSUS server for Windows and third-party updates each day or once a week at a scheduled time.
- Double-click Configure Automatic Updates in the Windows Update window.
- Select Enabled in the Configure Automatic Updates window.
Click the Configure automatic updating drop-down menu and select an update method for the managed computers.
The following table provides descriptions for each setting. Accept Auto download and notify for install (default setting) or select the setting that meets the deployment requirements.
Setting Description Notify before downloading and installing updates Patch Manager notifies you when updates are ready to download. Auto download and notify for install Patch Manager automatically downloads the updates and notifies the system administrator when they are ready to be installed. Automatically download updates and install them on the schedule specified below. Patch Manager automatically downloads the updates and installs them every day or on a specific day (such as Sunday) at a specific time. Allow local administrators to select the configuration mode that Automatic Updates should notify and install updates. Patch Manager allows only the system administrator to use the Windows Update control panel to select a configuration option (for example, Not Configured, Enabled, or Disabled). Local administrators cannot disable the Automatic Updates configuration. - Schedule a date and time for the installations.
Click OK.
The policy setting is displayed as Enabled in the Windows Update window.

-
Enable the Specify Intranet Microsoft Update service location policy setting in the group policy. This setting enables the managed computers to identify the Microsoft Update service location (or WSUS server location) where they can receive Microsoft updates from the WSUS server.
This setting is required to enable a WSUS server in the network.
- Double-click Specify intranet Microsoft update service location in the Windows Update window.
- Select Enabled in the window.
-
Enter the IP address of the WSUS server in both Options box fields.
If you do not have an intranet statistics server in the deployment, enter the WSUS server IP address in both fields.
Use the information in the table below to complete the Options box fields.
WSUS Server OS SSL Enabled? Enter this IP address Windows Server 2012
Windows Server 2012 R2
Windows Server 2016
Yes https://<ip_address>:8531No http://<ip_address>:8530Windows Server 2008 Yes http://<ip_address>:443No http://<ip_address>Windows Server 2008 systems use port 80 by default
-
Click OK.
The policy setting is displayed as Enabled in the Windows Update window.

The GPO is configured on the targeted domain.
