Enable alerts for suspected cases on ransomware on file servers
Background / Value
To efficiently capture security incidents, ARM focuses on user-initiated file server events. If these occur in unusually high numbers and additionally in a short period of time, ARM proactively informs all those responsible.
Ransomware Attack: The combination of file creation and deletion by one user account.
Related features
Enable alerts for file server directories
Enable alerts for suspected data theft (file server)
Enable alerts for data deletion (file server)
Step-by-step process
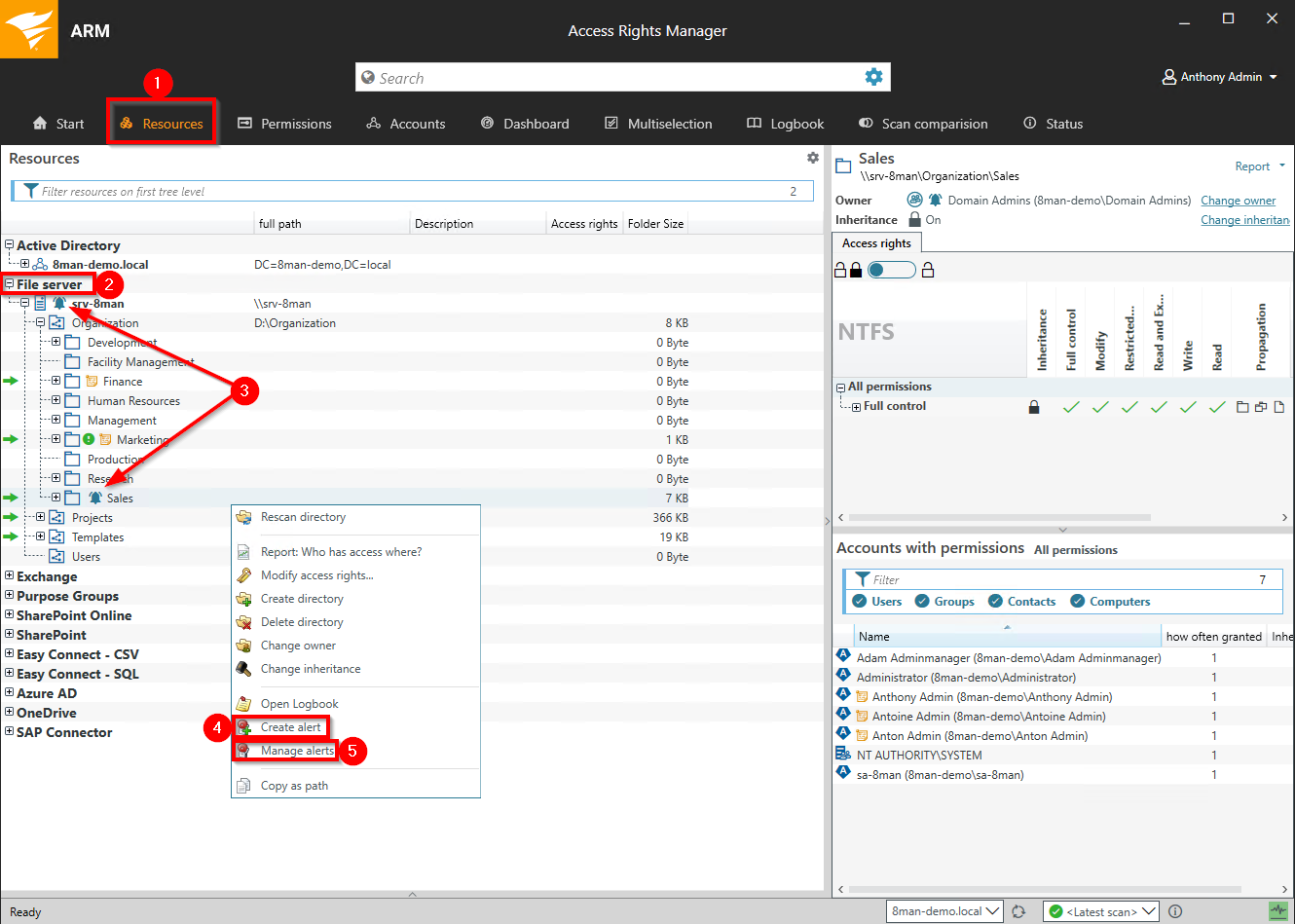
- Choose Resources.
- Expand File server.
- Already configured alerts are displayed with a bell symbol.
- Right-click on a resource and select Create alert in the context menu to create a new alert.
- Right-click a resource and select Manage alerts in the context menu to customize or delete existing alerts.
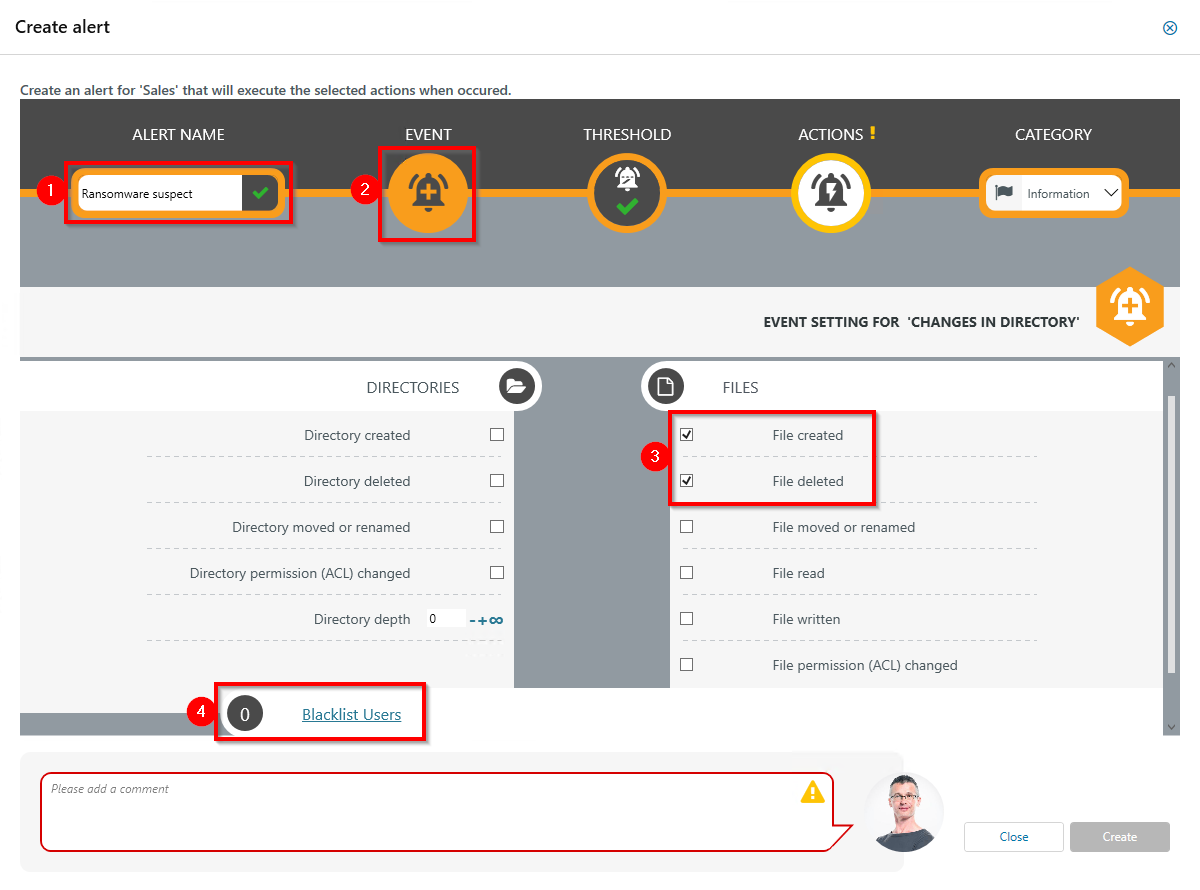
- Give the alert configuration a name.
- Click Event.
- Define which events trigger an alert. Typical for ransomware: a combination of File created and File deleted.
- Optional: Click Blacklist users.
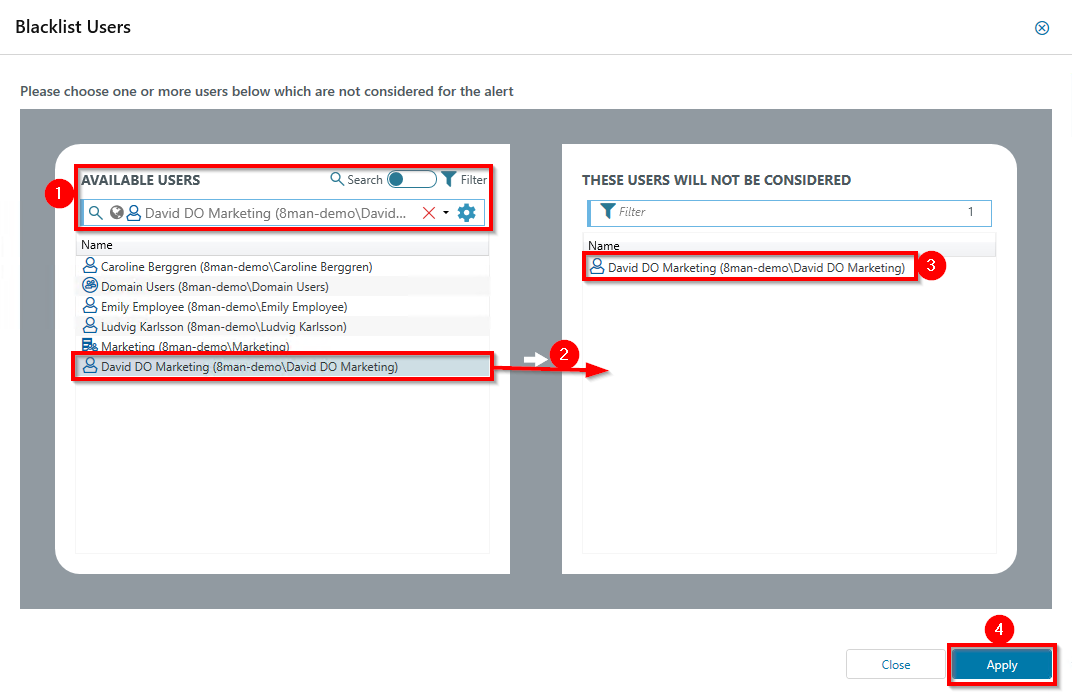
Optional: Use the blacklist to define which users do not trigger an alert.
Each alert configuration has its own blacklist configuration.
You can only add users, not groups.
- Use the search function to find the users you want.
- Use double-click or drag-and-drop to add users to the blacklist.
- Use the DEL key to remove users from the blacklist.
- Click Apply to save the changes.
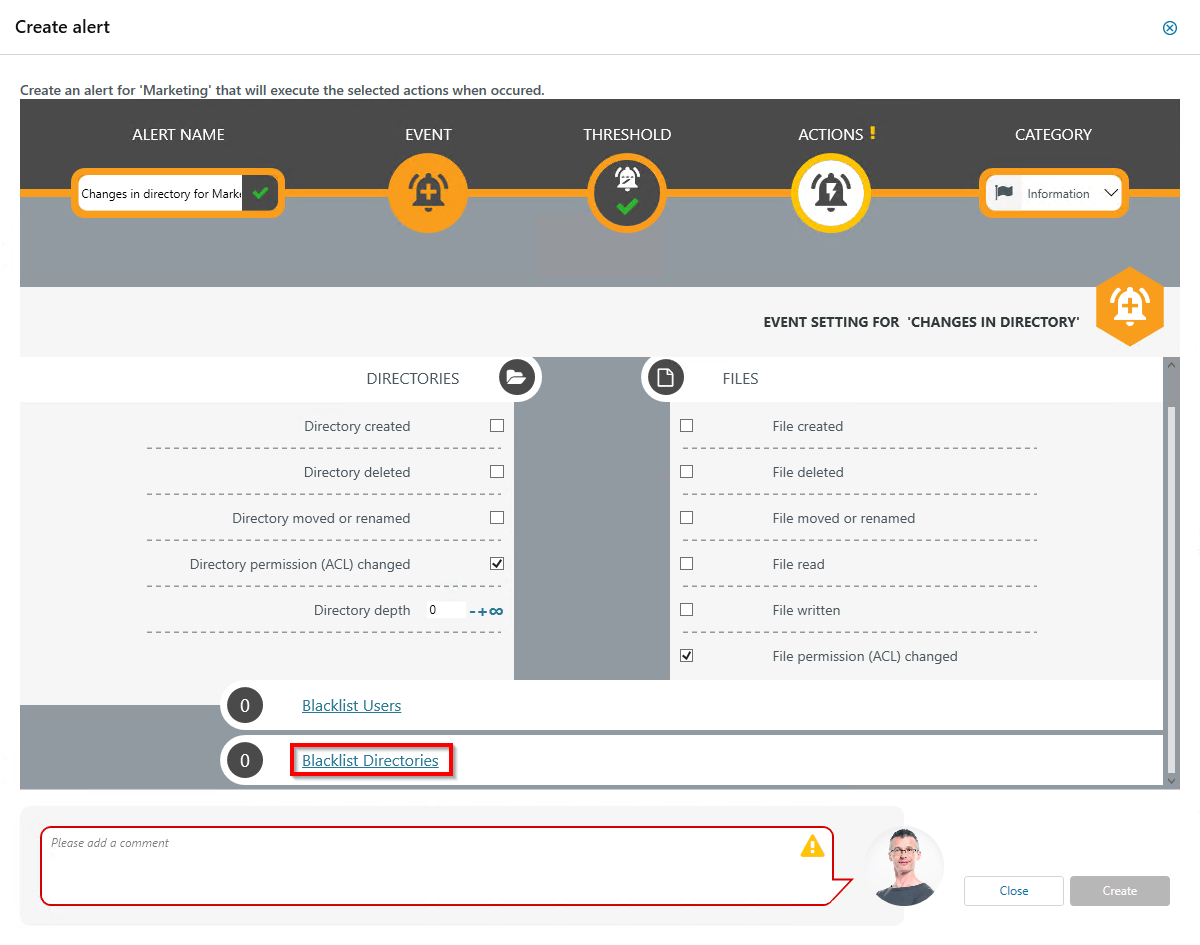
Optional: Select Blacklist directories.
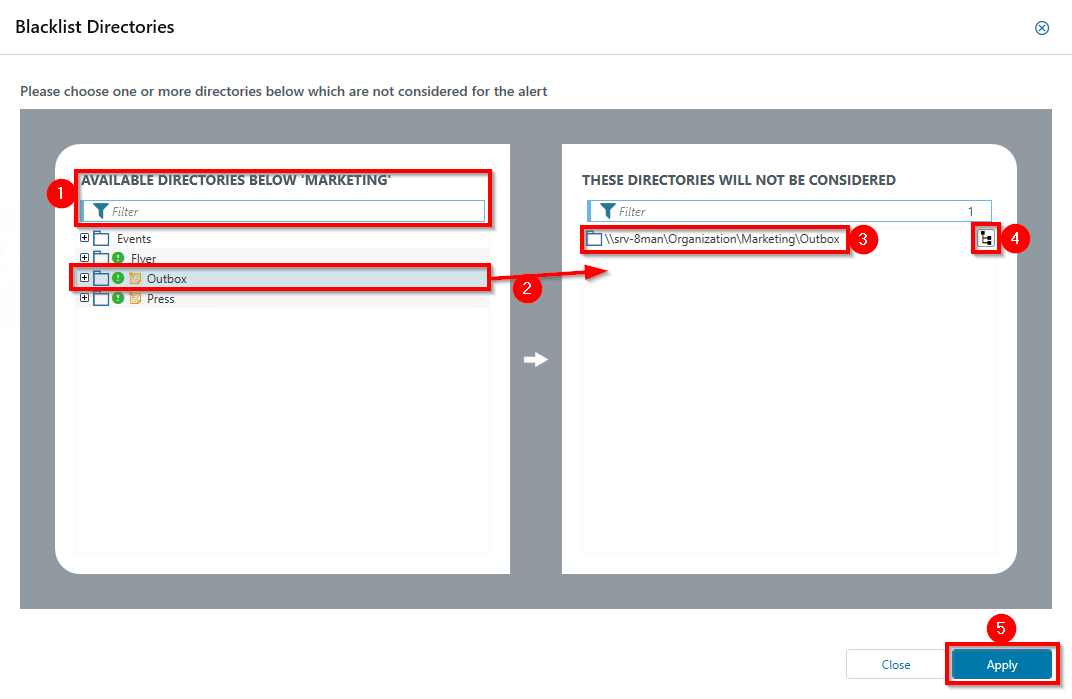
Optional: Use the blacklist to define which directories are not monitored.
- Use the filter function to find the desired directories. When you filter, the tree view changes to a result list of the directory paths.
- Use double-click or drag-and-drop to add directories to the blacklist.
- Use the DEL key to remove directories from the blacklist.
- Enable or disable monitoring of subdirectories.
- Click Apply to save the changes.
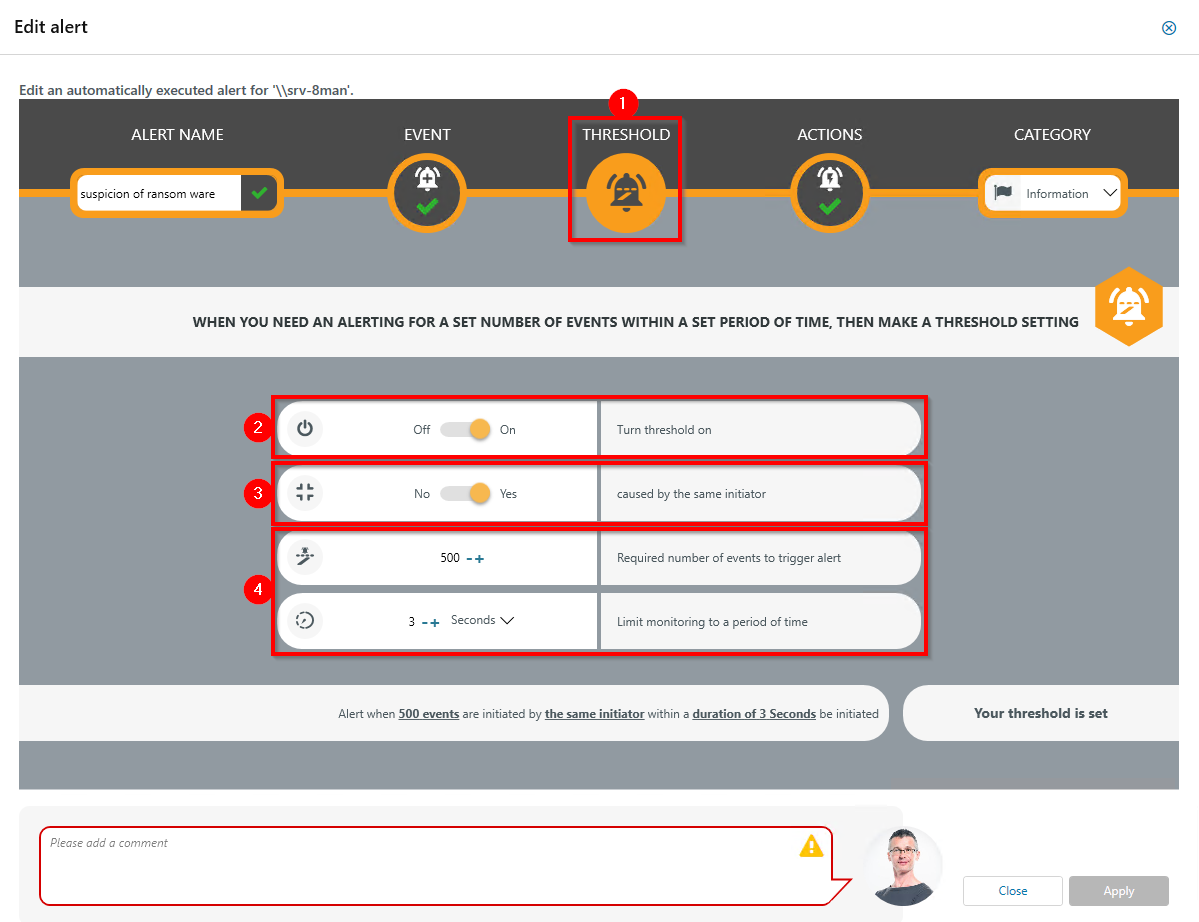
- Select Threshold.
- Enable threshold.
- Activate the option. When ransomware is suspected, typically all events are triggered by the same user.
- Define how many events within a period trigger the alert.
Defining a threshold with a large number of events over a long period of time will consume a lot of memory (RAM). We recommend that you configure time intervals as small as possible.
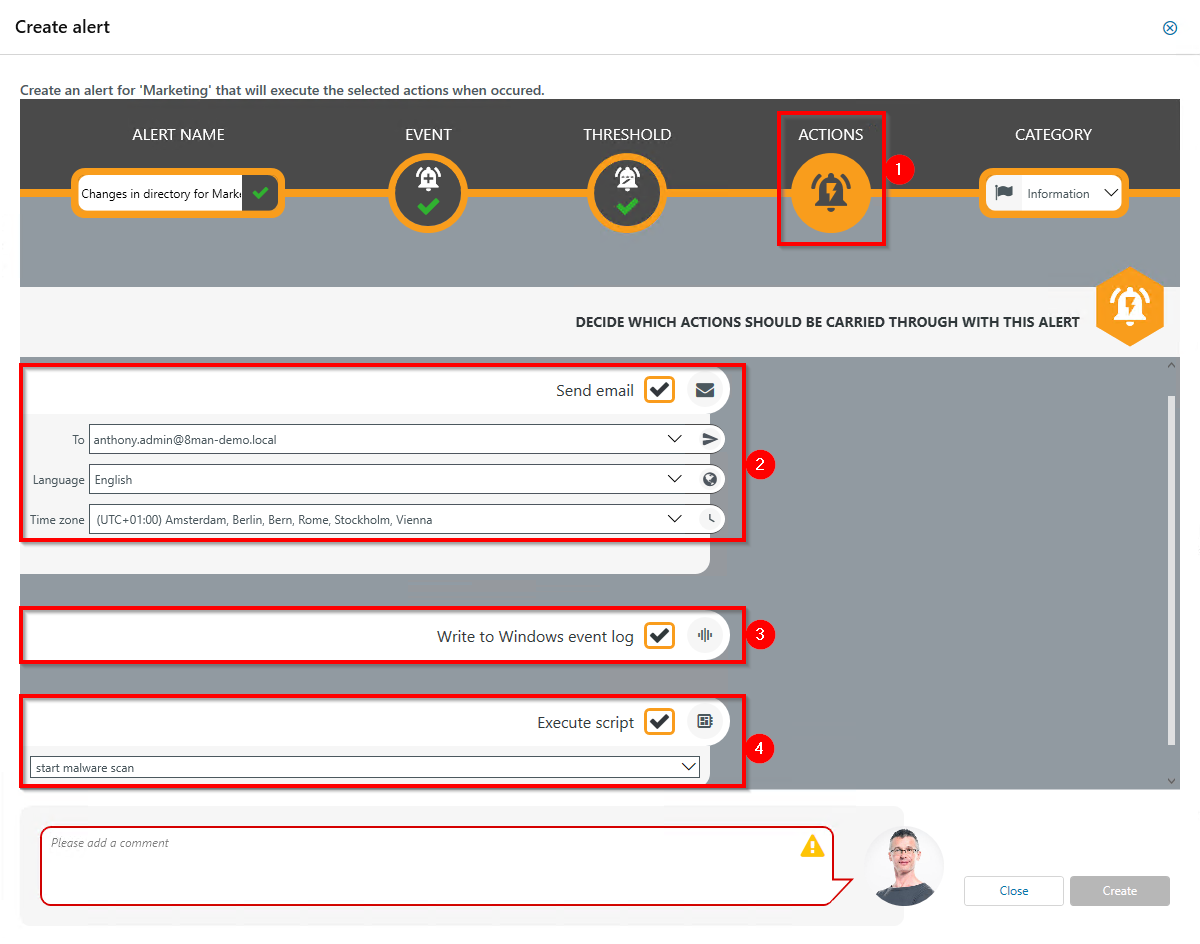
- Choose Actions. Here you specify which actions are executed when an alert is triggered. You must activate at least one action (arrows).
- Activate the option if an email should be sent in case of an alert.
The content of the emails can be customized. This is analogous to the recertification emails.
- The alert is written to the Windows Event Log. The categorization is used.
- Enable the execution of a script. To activate this option, a script configuration for alerts must be stored.
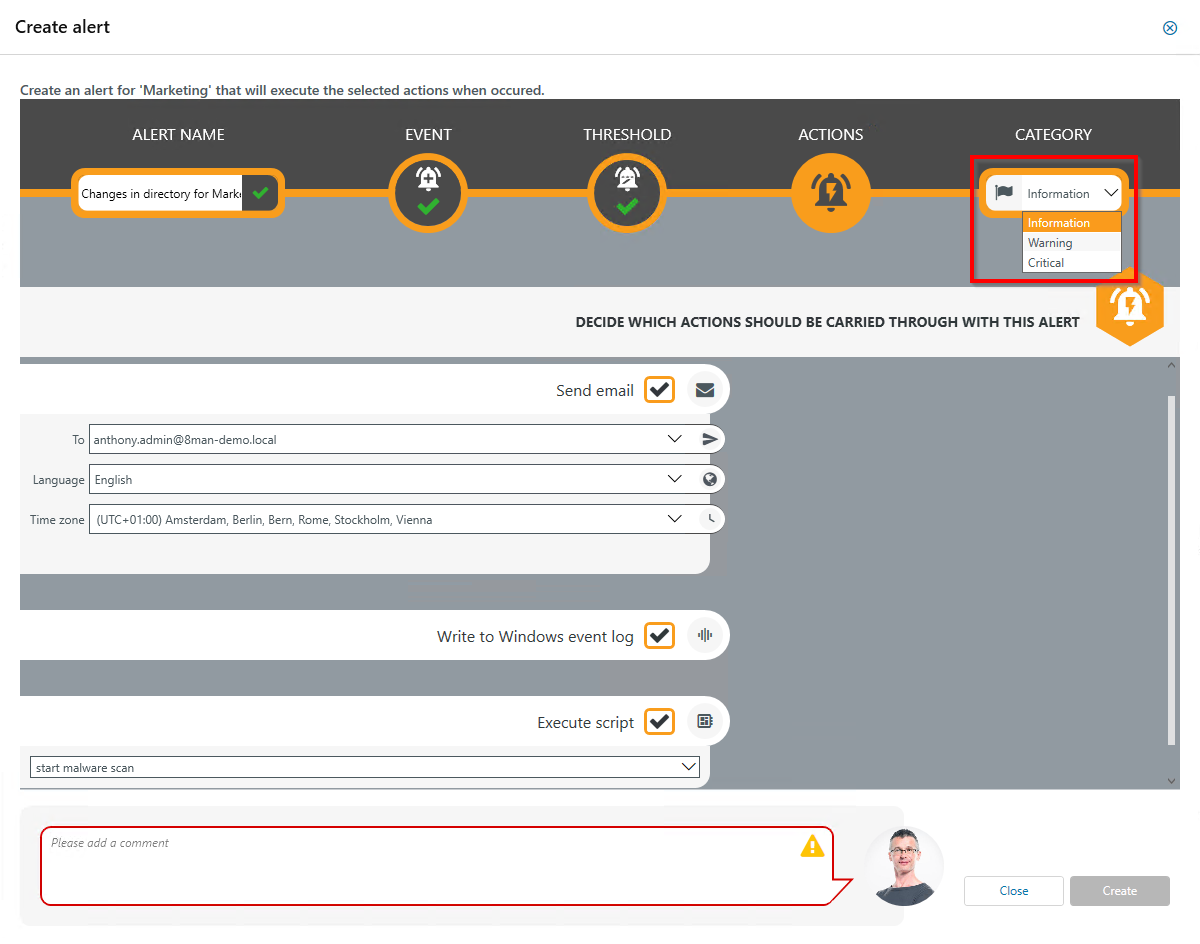
Choose a category. This is used when writing to the Windows Event Log and for the email subject.
This option is especially useful if you are using a SIEM system.
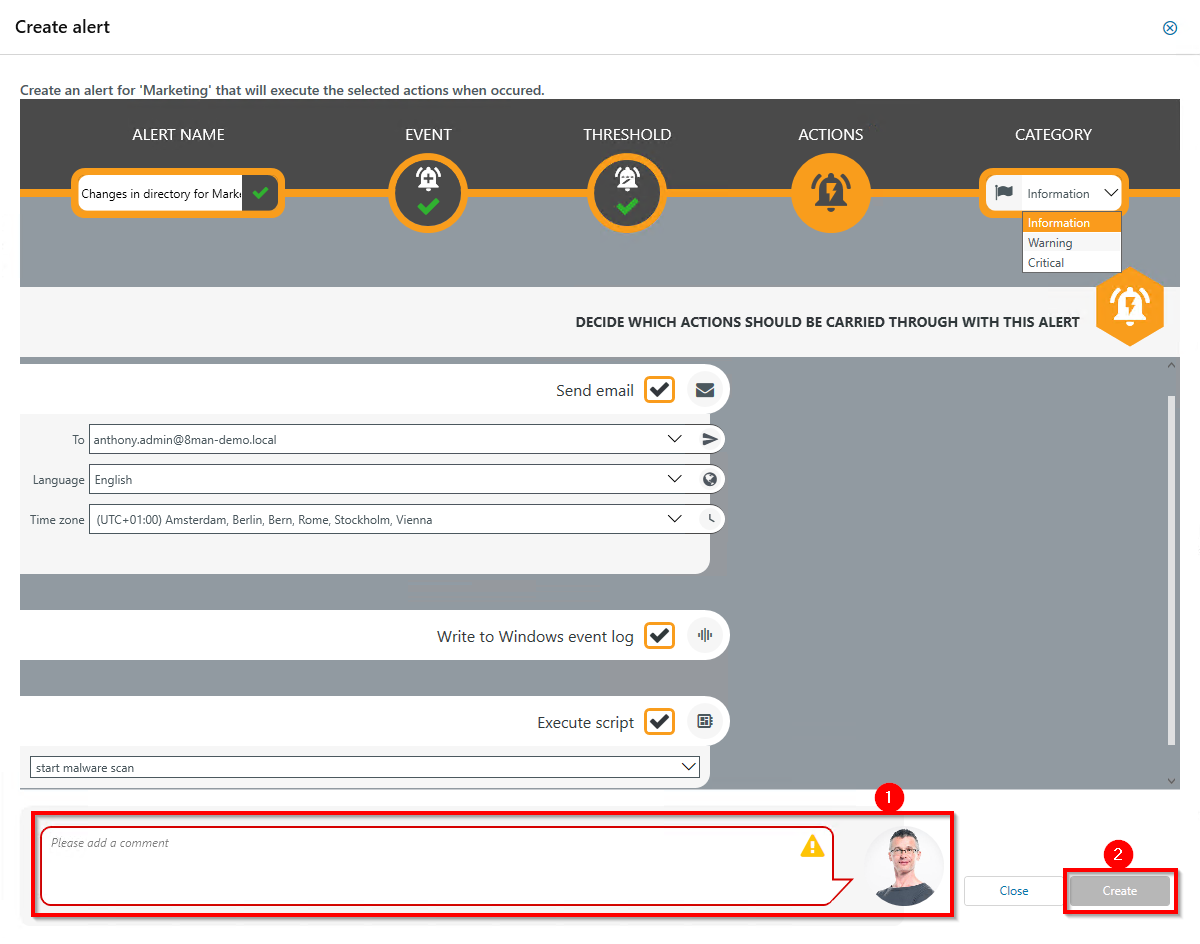
- You must specify a reason for the alert configuration in order to save it.
- Click Create.
