Define file server and share specific change settings
You can configure specific settings for each file server and configured shares:
- the account used to make the changes
- in which domain the Access Rights Manager groups are stored
- the Group Wizard Settings (access categories, group naming conventions, blacklist)
- how the list rights are managed.
If you do not set any optional Group Wizard settings, the parent level settings will be used.
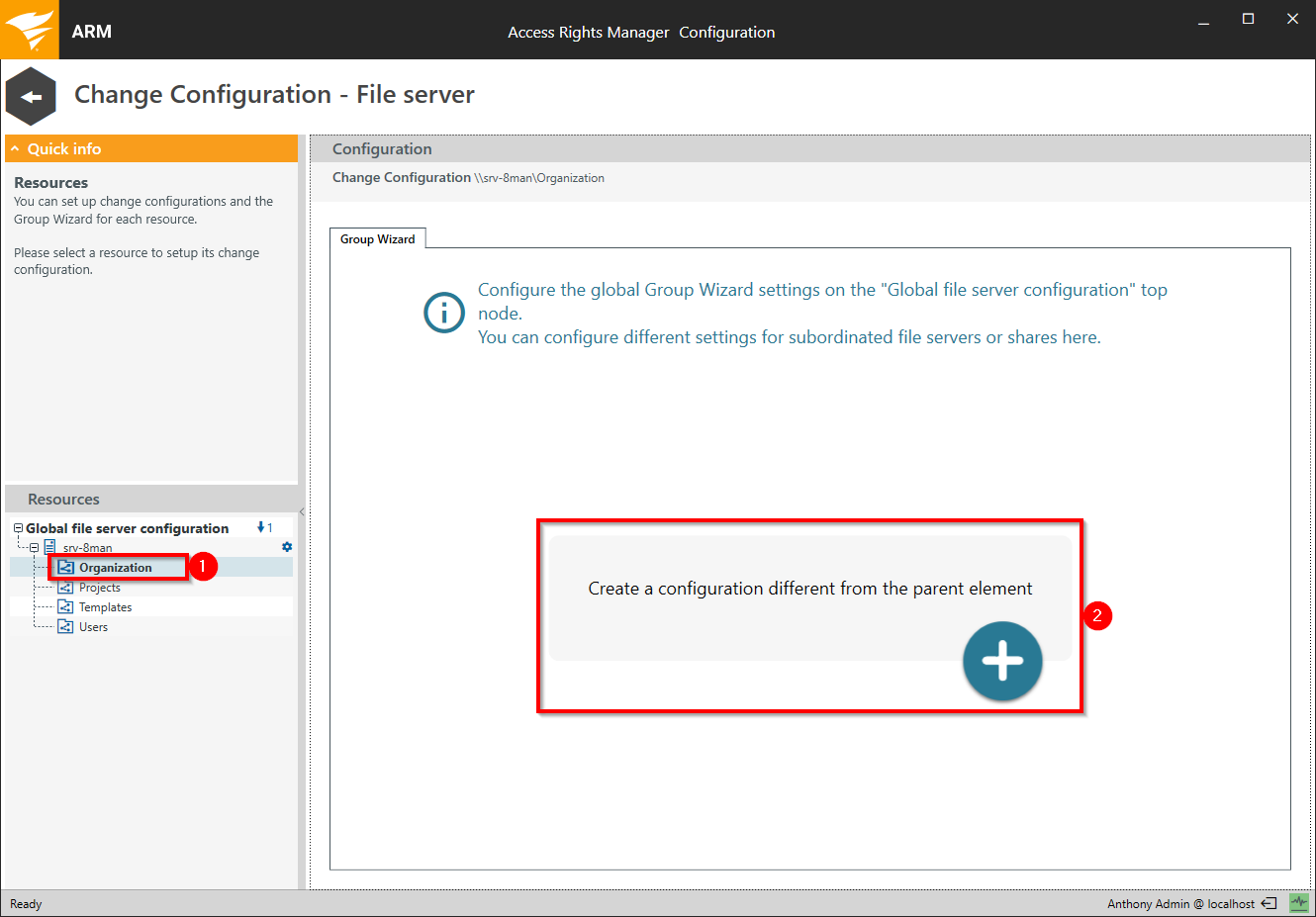
- Select the desired file server or share in the "Resources" area. How to add a file server is described in the chapter Add FS scans. Newly added file servers and shares do not have a configuration.
- Create a new configuration.
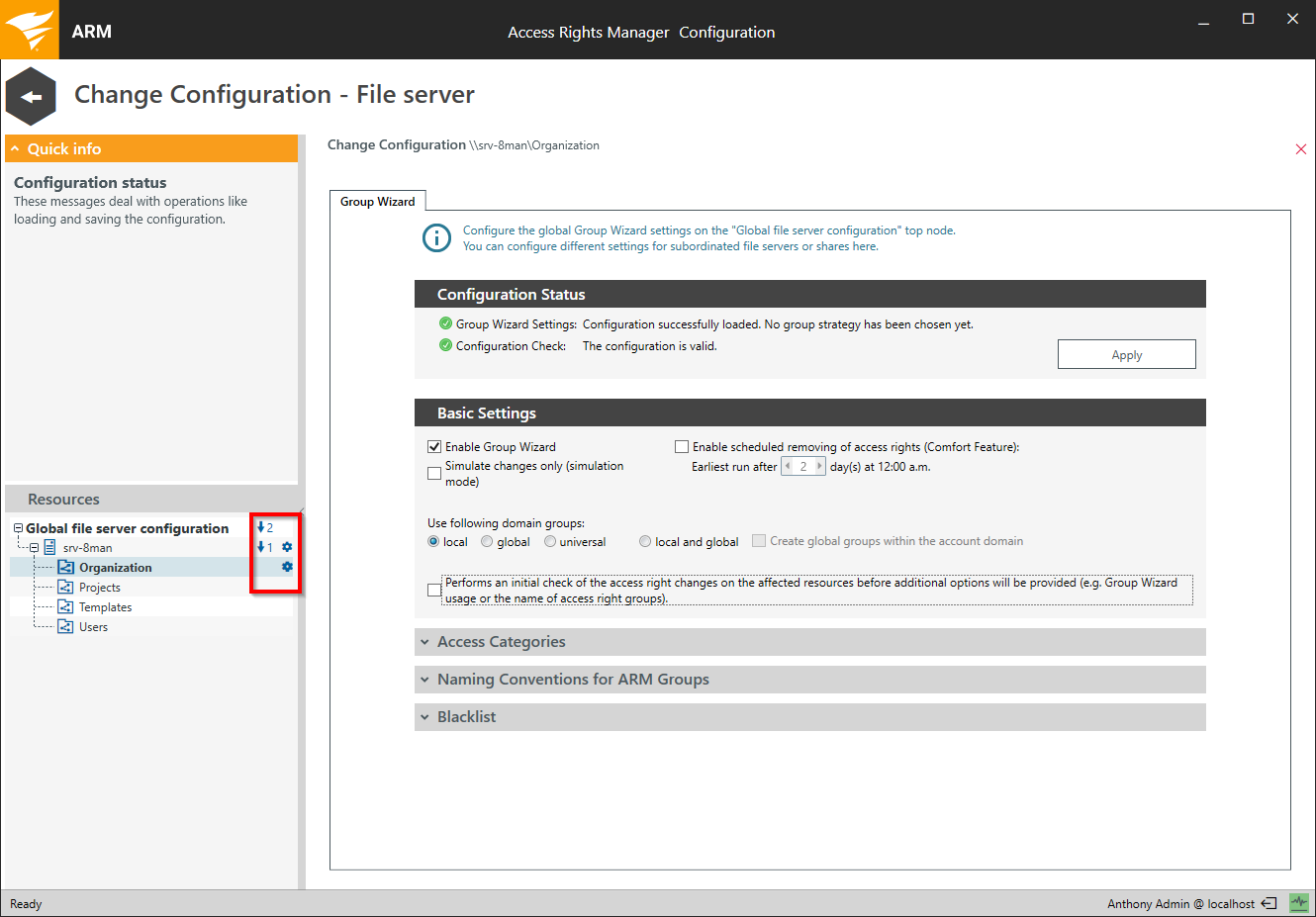
Access Rights Manager shows you how many configurations exist below (arrow with number) and where they are (gear).
Configure the FS change account
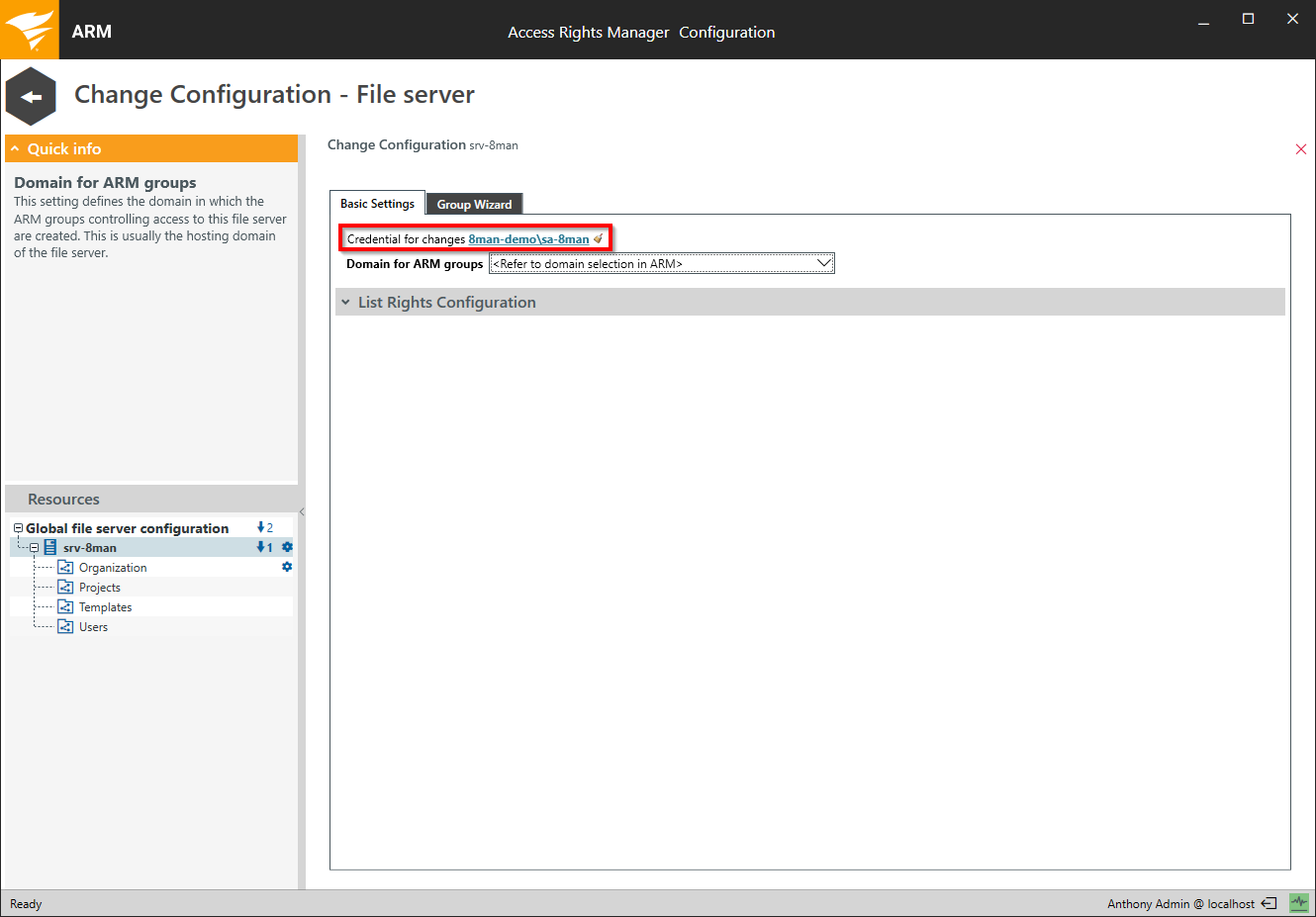
Determine which account is used to apply changes to the selected file server resource.
If you don't enter credentials these will be requested in the Access Rights Manager application.
Determine the domain for ARM groups
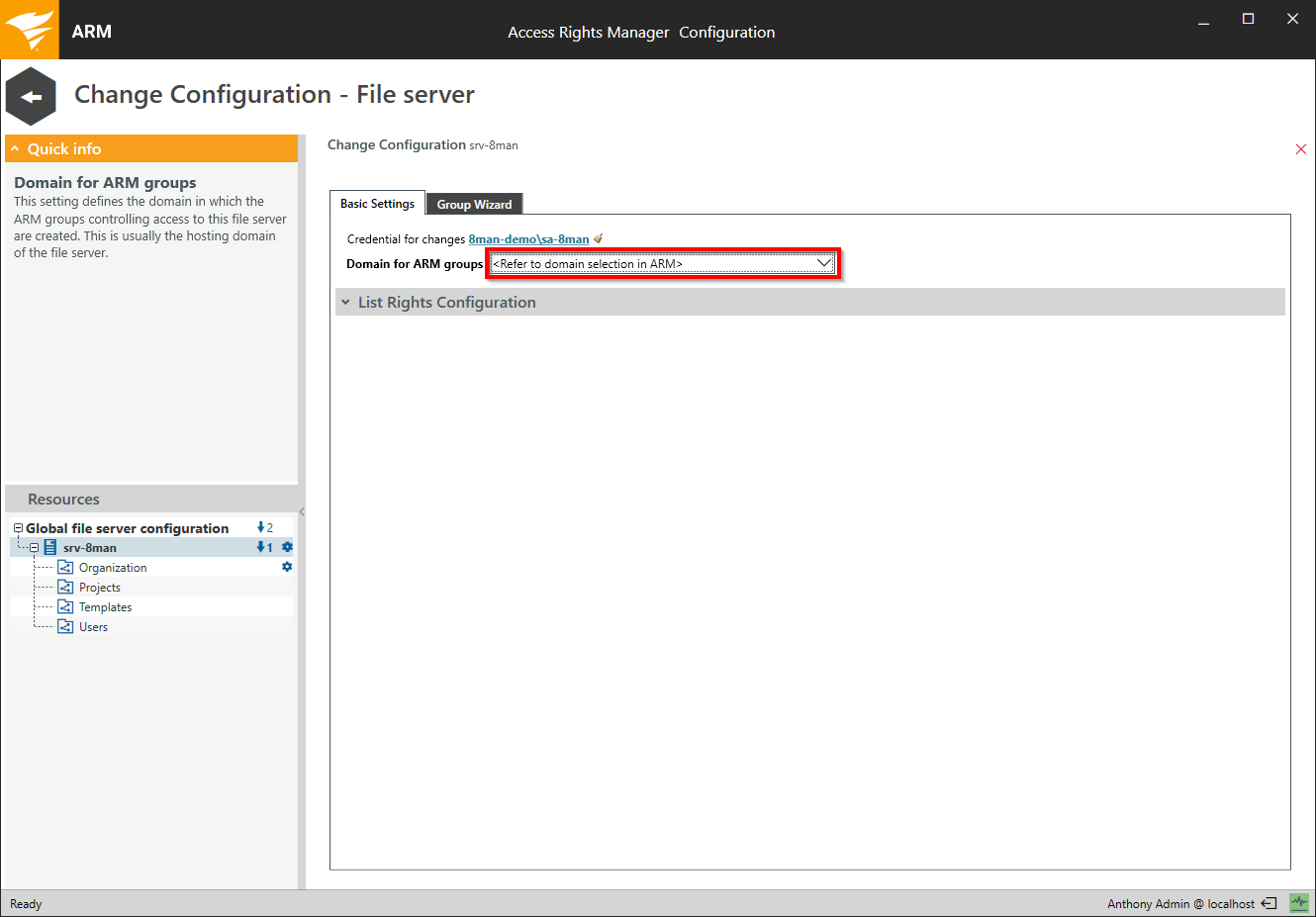
Select the domain in which the Access Rights Manager groups are stored.
If you don't enter a domain, the Access Rights Manager-groups will automatically be stored in the domain that the user has selected in the Access Rights Manager application.
Configure automatic list rights management
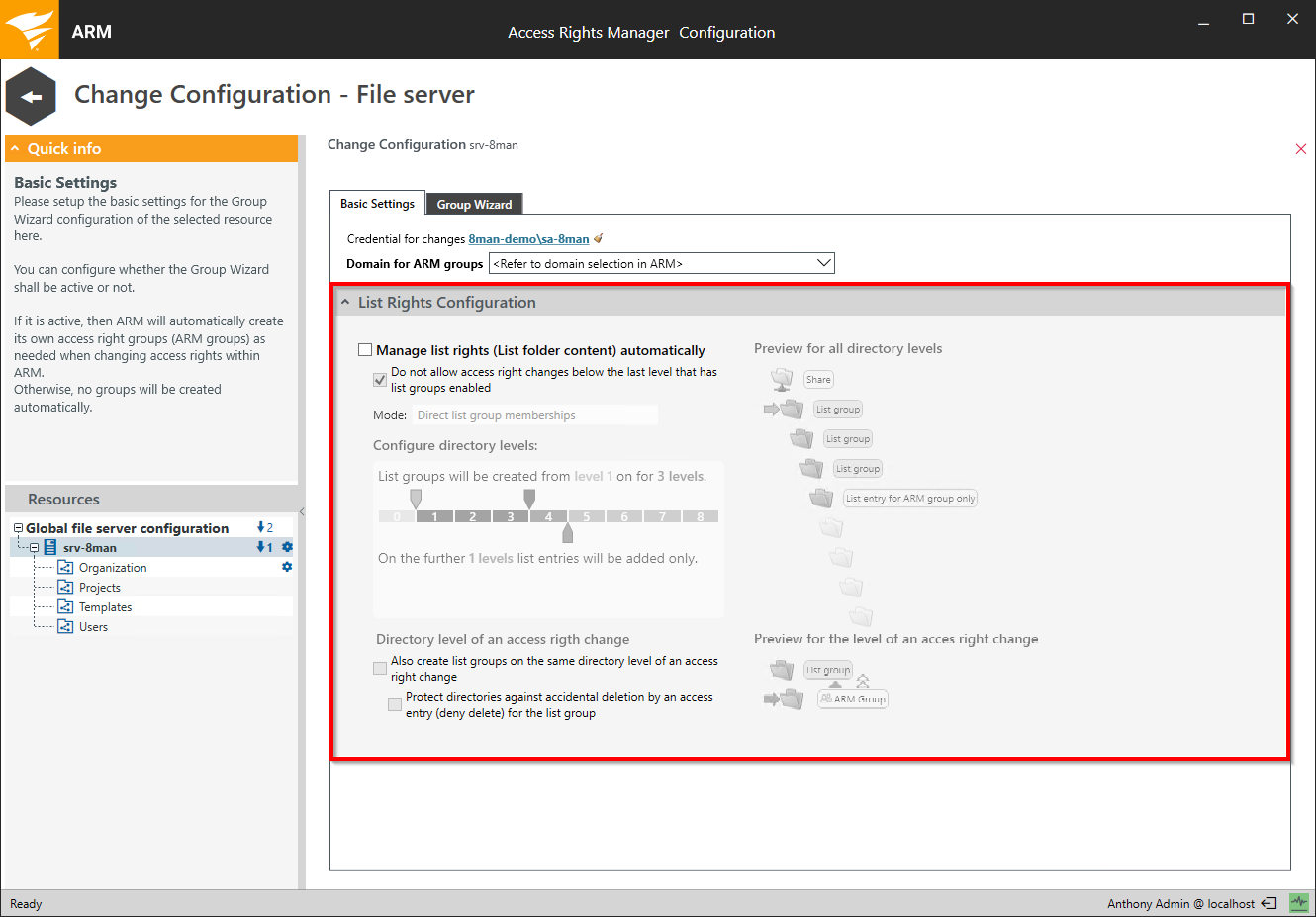
The list right configuration includes several options for determining how Access Rights Manager automatically ensures that users can navigate to the folders that they have access to.
Compared to Microsoft native tools you can avoid many cumbersome and error prone administrative steps.
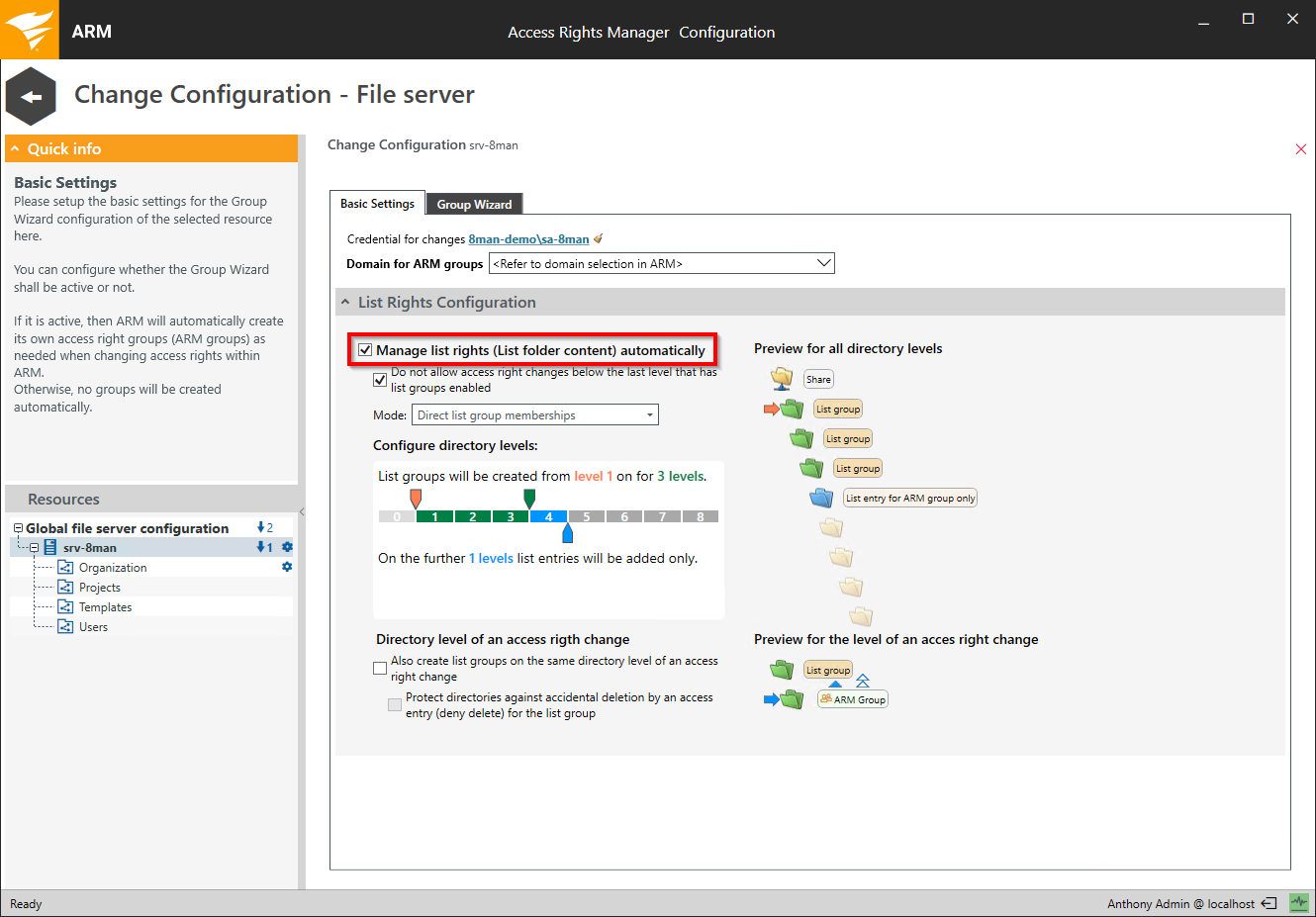
Activate the automatic list rights management.
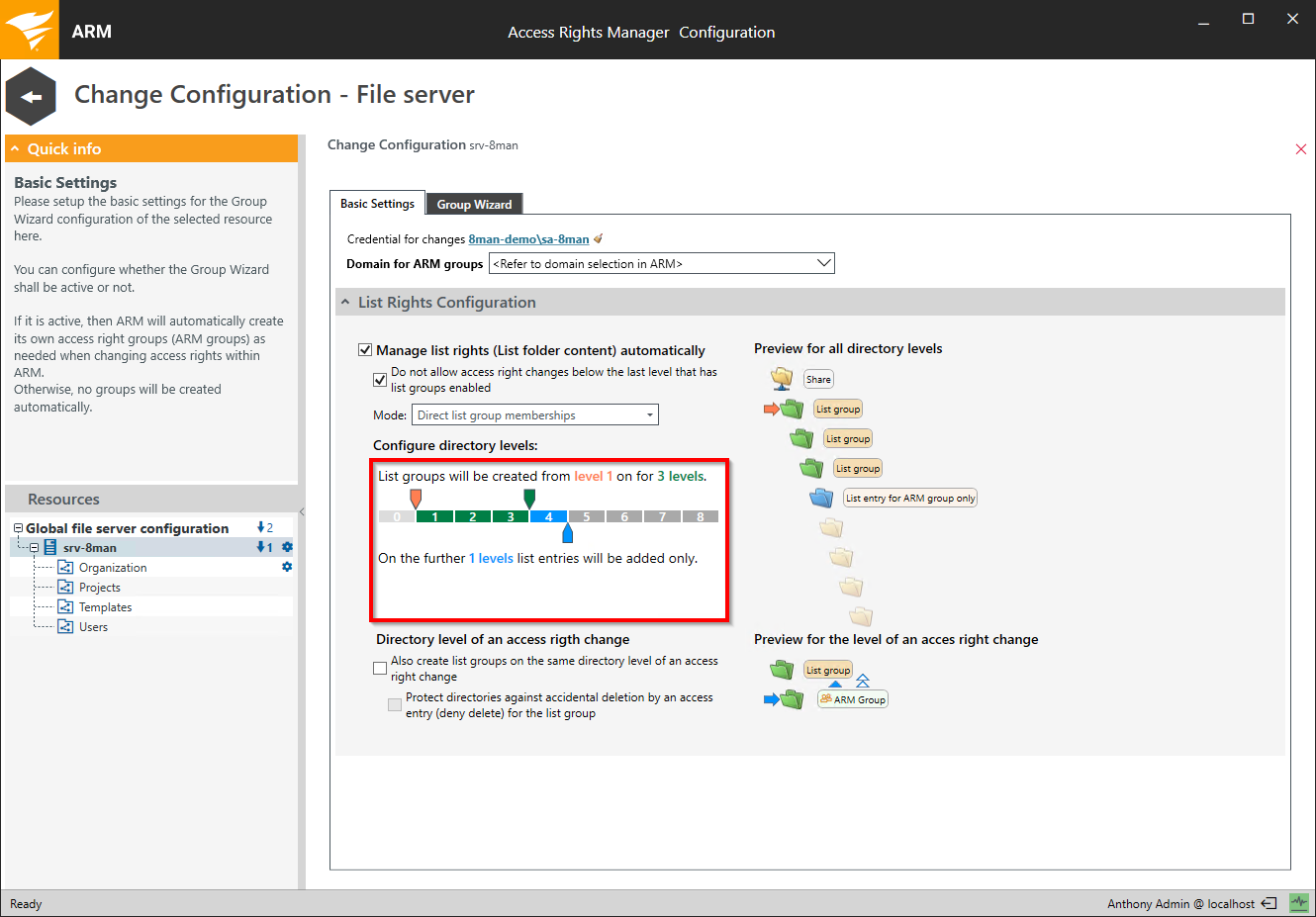
Use the sliders to determine the level of folder depth that Access Rights Manager manages.
Level 0
Level 0 is the shared folder (share level). This folder is visible to users based on share rights. An assignment of list rights on this level is not required.
green levels
Access Rights Manager creates list groups for every level. The access rights groups become members of list groups.
blue levels
Access Rights Manager does not create list groups for these levels. Access groups are provisioned by entering list rights directly into the Access Control List (ACL). This way overall less groups are created and Kerberos token size is minimized. On the other hand more ACL entries are required which may cause file server performance issues.
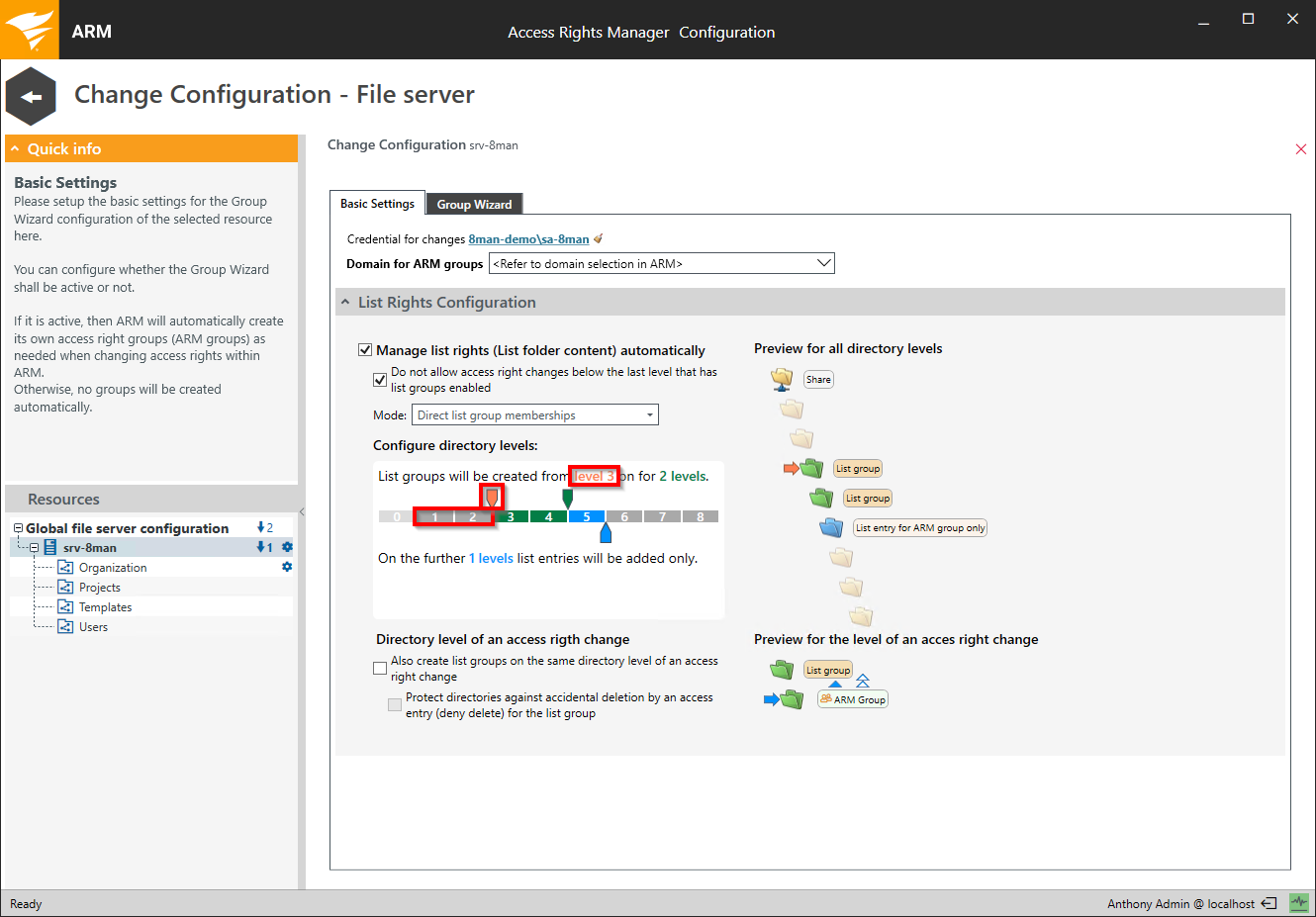
Move the orange slider to exclude folder levels from the automatic creation of list groups. This is useful if users already have list rights to these folder levels.
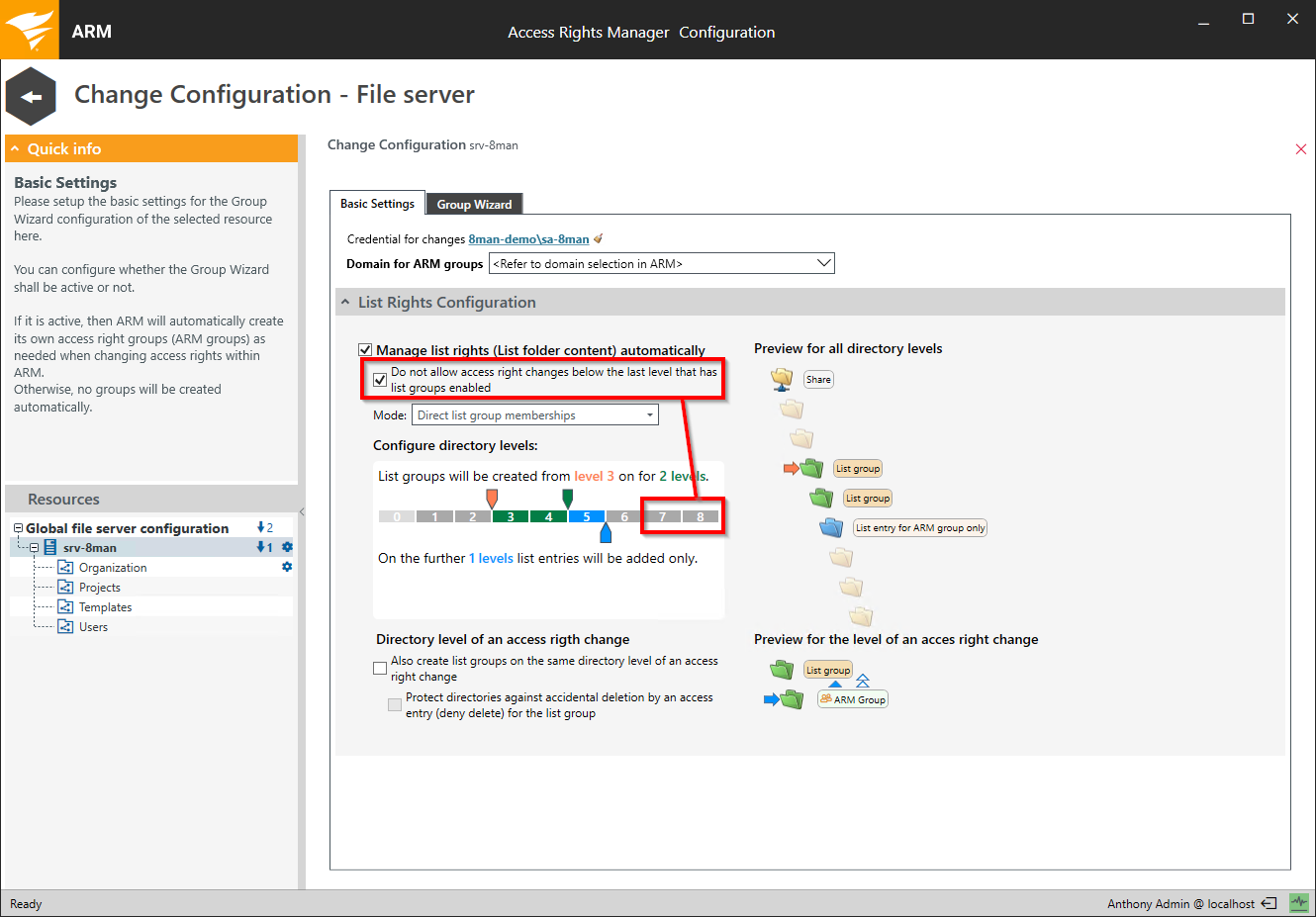
Activate this option to prevent access rights changes with Access Rights Manager below the lowest "list-rights-level" plus one (for example level 7, as in the screenshot).
You should activate this option to prevent users from gaining access to levels that they are not able to navigate to.
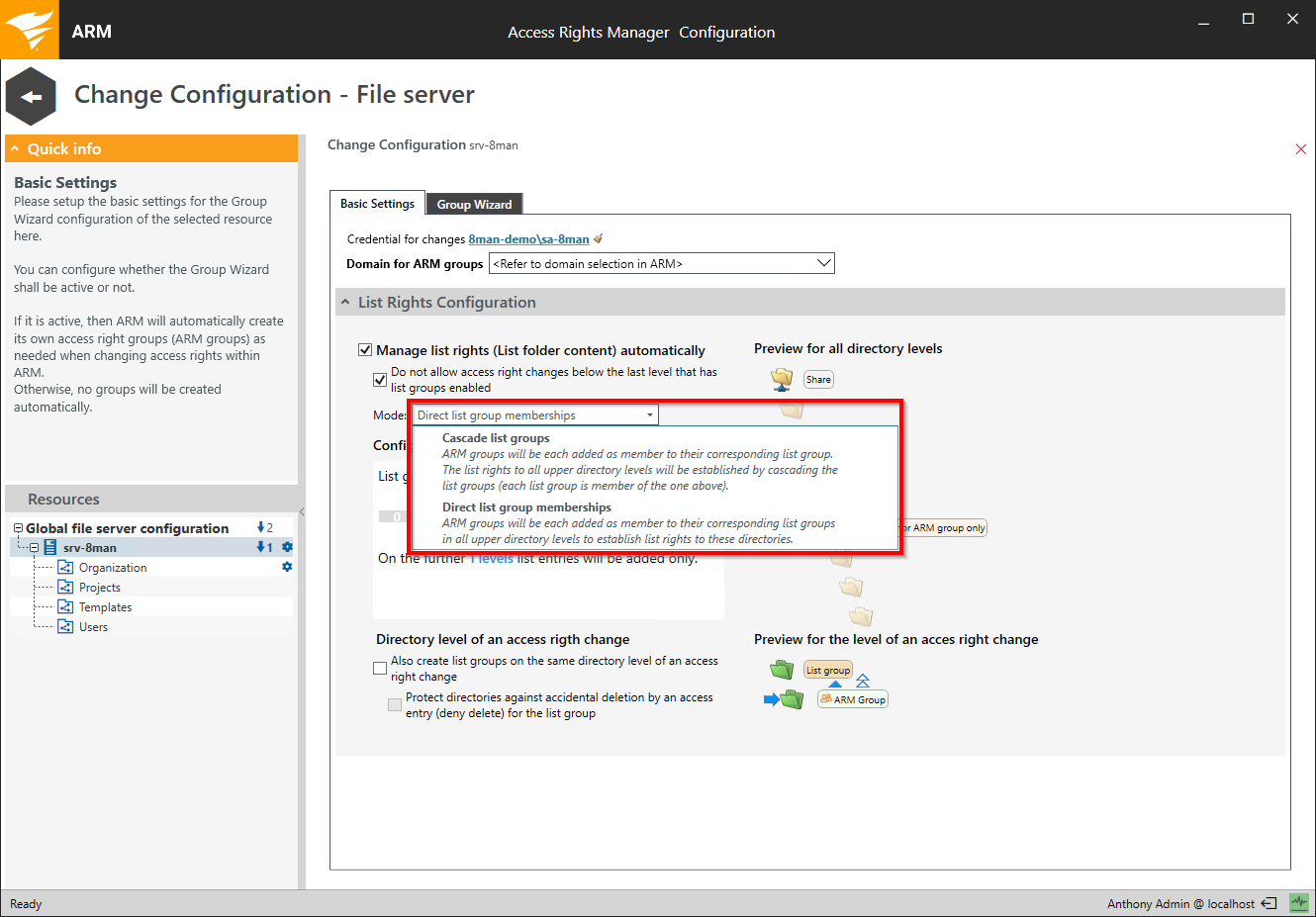
Select a list group mode.
This setting has no impact on Kerberos token size.
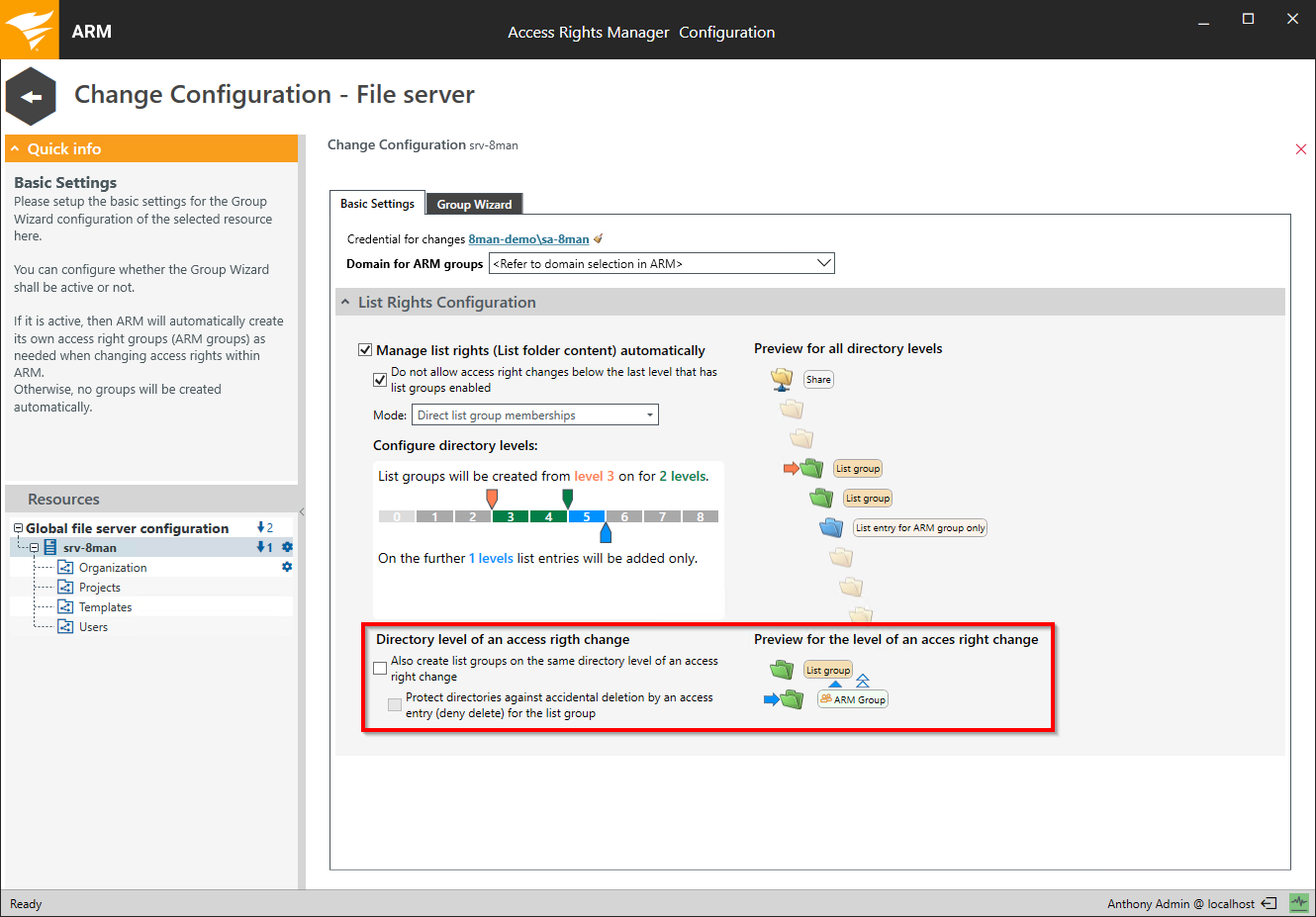
You can use these options to prevent the deletion of folders that are to be retained as parents for inheritance.
It is more beneficial to protect folder levels by assigning "restricted modify", as these require fewer group memberships.
Delete a file server- and share-specific change configuration
Click the red X to remove a change configuration.
