Configure Single Sign-On (SSO) via SAML
SolarWinds Application Management products — Loggly, AppOptics, Papertrail, and Pingdom— support single sign-on (SSO) via SAML 2.0 integration. SAML (Security Assertion Markup Language) is an industry standard used to provide single sign-on by authenticating against a particular identity provider (IdP). Users can log into their Active Directory domain or intranet and have immediate access to these SolarWinds products, without requiring additional log-in.
When SSO is enabled, organization members must authenticate against IdP, unless the user account is identified as a service account. Service accounts are allowed to log in with a separate username and password. See Set up service accounts.
Configure SAML
The organization owner can configure SAML in the Security section of the Application Management products’ common settings. Click Settings, select Account, and click Enable SAML to access the Security section.
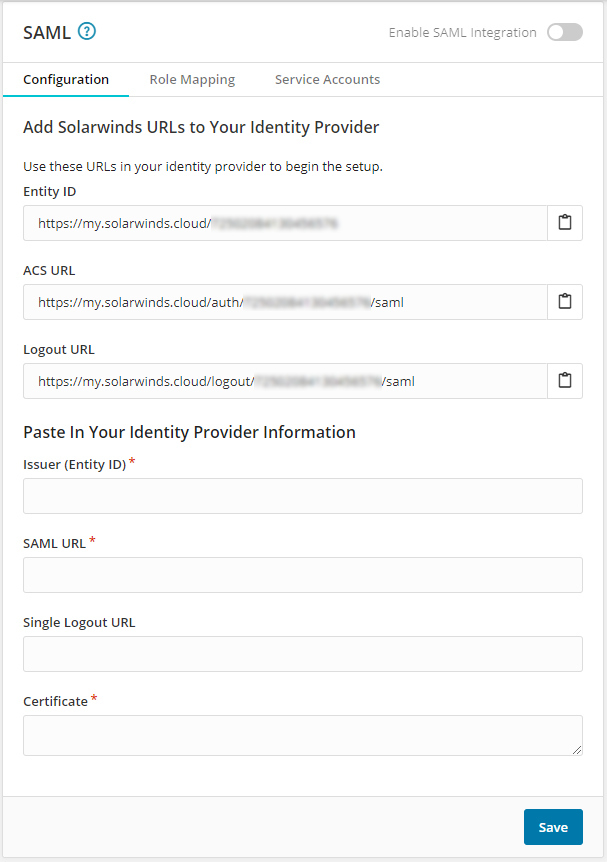
Integrate SAML
- Use the three SolarWinds URLs when configuring your Identity Provider (IdP) for integration with SolarWinds Application Management products.
Find the following information from the Identity Provider and enter it in the fields provided:
- Issuer (Entity ID)
- SAML URL
- Single Logout URL (optional)
Identity Provider X.509 certificate, provided in a PEM format with a proper prefix and suffix. See example below.
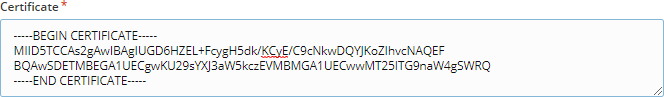
- Save the configuration.
Click the toggle on the right side of the SAML pane to enable SAML integration for the organization. Organization members except the owner will be logged out of all SolarWinds Application Management products.
Organization members can log in either via the IdP or the dedicated login screen that is available from the login screen (see Log in with SSO credentials).
If a user is removed from your IdP and removed from the list of service accounts (if applicable), the user’s access to your organization and its data is removed. The user is still listed as a member of the organization in the Users screen of the Organization Settings but has no products enabled. See Remove a user from your organization for more information.
SSO configuration information for various identity providers
SSO configuration can vary between Identity Providers. The following list provides links to the appropriate IdP documentation:
When configuring your IdP, the following user attributes should be set:
givenname,givenName,firstname, orfirstName: optional. If set, will overwrite the first name set in the user’s profile.surname,surName,lastname, orlastName: optional. If set, will overwrite the last name set in the user’s profile.NameID: required if users will log in via the IdP’s portal page. Value should beuser.emailgroupsorGroups: Required only if setting up role mapping. Otherwise, do not use this attribute. See Set up role mapping.
Additional SAML integration information
If SAML integration is disabled, legacy users (those who existed in the organization before SAML was enabled) should use their original password to log into the product. Users added after the integration will have to perform a password reset.
The organization owner can invite new Application Management users known to the IdP into the SAML-enabled organization or use role mapping to grant immediate access all users in an IdP user group.
Set up role mapping
Role mapping allows you to define organization and product roles, as well as grant access to logs and billing plans, based on the account’s IdP group membership. Members added to an IdP group will automatically gain access to any organization or product role mapped to that group.
- Organization Roles define the access users have to the organization’s settings and resources across all SolarWinds Application Management products (AppOptics, Loggly, Papertrail, and Pingdom).
- Product Roles define the access users have to the individual product’s data and settings, including which log groups users can access.
Users must have an organization role defined before they can log into a SolarWinds Application Management product. If role mapping is enabled, ensure all users are members of a group mapped to an organization role. If users are only mapped to product roles, they will not be able to log into the product.
If a new user is added to a mapped IdP user group, a SolarWinds Unified Login account will be created for the user automatically.
Organization owners cannot be defined via Role Mapping. See Manage Users for instructions detailing assigning the owner role to users manually.
To map roles to group memberships:
-
Update your IdP configuration so it sends the correct groups. Configure the SAML Assertion that is sent to the SolarWinds Application Management products to send the IdP group to an attribute named
groupsorGroups.This configuration will vary depending on your IdP provider.
This setting is required to map IdP groups to organization and product roles. If the groups membership is not configured correctly you will see a “No SAML groups received” error.
-
In the Security section of the Application Management products’ common settings, select the Role Mapping tab and click Enable Role Mapping.
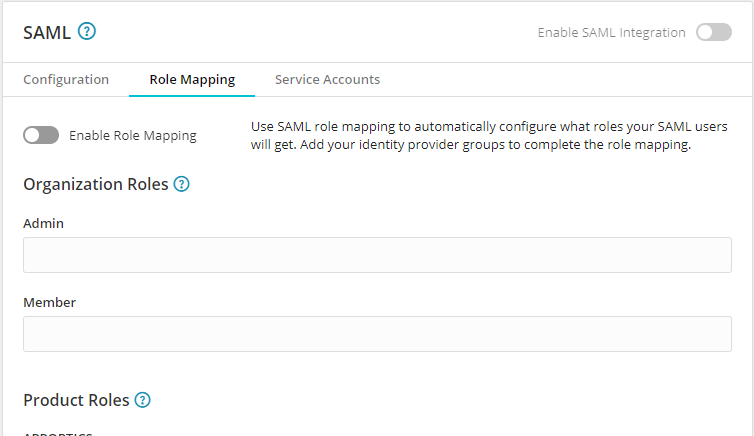
- To map an organization or product role, select the field for the role you wish to map, type the name of an identity provider group, and press enter. For details about the Organization Roles and each product’s Product Roles, see User Roles and Access Levels.
When role mapping is enabled or disabled, all organization members except the owner will be logged out of the Application Management products (Loggly, AppOptics, Papertrail, and Pingdom).
Every time an organization member logs into an Application Management product, the organization’s IdP is accessed and read.
Set up service accounts
With service accounts, users can log in to SolarWinds Application Management products with either their SAML login or their SolarWinds Unified Login account’s username and password. Organization owner accounts are automatically included as a service account.
To define a user account as a service account and allow the user options for how they log in, click the Service Accounts tab and type the user’s email address in the Accounts field or select the user from the dropdown.
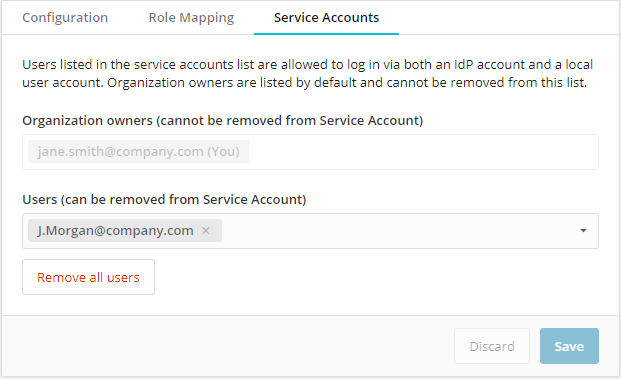
Once all service accounts are defined, click Save.
If a user account was defined as a service account and is later removed from the IdP, their service account status will still allow them to access the organization. Remove the user account from the list of service accounts to ensure access to your organization is revoked.
Log in with SSO credentials
Click Log in with Single Sign On from the Papertrail login page, enter your organization email address, and click Log in with Single Sign On. If you are not already logged into your identity provider, you will be prompted to log in with your identity provider. Once you are logged in, you can access all organizations that you are a member of. See SolarWinds Unified Login for more information.

FAQs
What is SSO/SAML?
Single sign-on (SSO) is an authentication method that allows users to log in to several independent software systems with a single set of credentials. Security Assertion Markup Language (SAML) is a protocol used to configure and implement SSO. This (single) authentication is provided by an identity provider. Once the user is authenticated against the identity provider, they are automatically authenticated to use all configured services. This helps administrators manage users’ access to multiple services and allows users to access multiple services without worrying about multiple login credentials.
In layman’s terms, SSO/SAML allows users to access multiple software systems, including Papertrail, using their corporate login method.
When the term SAML is used in this document or in the software, it is referring to the SAML authentication method used by Papertrail to implement SSO.
What is an IdP?
IdP stands for identity provider, which is a service that stores and manages user accounts. Identity providers allow companies to securely manage access to their systems and data. SSO/SAML uses an identity provider to authenticate user accounts across multiple services.
Examples of identity providers include Microsoft Azure, Google, OneLogin, and Okta.
What are Organization Roles and Product Roles?
Organization Roles define the access users have to the organization’s settings and resources across SolarWinds Application Management products (AppOptics, Papertrail, Papertrail, and Pingdom). Organization Roles take precedence over Product Roles.
- Member roles have access to viewing the organization’s resources, but cannot modify settings related to the organization.
- Admin roles can also manage the organization, its users, the products activated, and the organization’s settings.
- Owner roles can do anything a member or admin can do, but also are allowed to configure Security settings.
If a user or group is assigned to multiple roles, the role with the greatest access will be applied.
Product Roles define the access users have to the individual product’s data and settings. For Papertrail, the user role has access to log data; depending on the restrictions applied to the user in Papertrail settings, access to that data may be limited to a set of specific source groups. An admin in Papertrail has access to all log data, as well as the ability to manage users and account settings. The owner role can also update billing details, modify subscription settings, and cancel the Papertrail organization.
Why are my organization’s users asking for me to create service accounts for them? Should I do it?
Service accounts allow users to log into Papertrail with a username and password instead of using the SAML-authentication method you have set up. Whether or not you create a service account for a user depends on the following:
Do you need to audit user access to a product? Disallowing service accounts allows you to audit login access from one location – your IdP.
- How much manual user management and support are you willing to perform? Creating a service account for users means paying attention to which users can log in with only SAML versus those that can log in via either SAML or username and password. Also, when revoking a user’s access to Papertrail, you need to remove them from both the IdP and the list of service account users; if a user is no longer a member of an IdP but has a service account defined, they still can access Papertrail.
- Do you need to grant users not in your company’s IdP access to your Papertrail organization? Creating a service account for that user would allow these users to log into Papertrail without authenticating against your company’s IdP.
- Does your user access multiple organizations? If the organization owners for each of their organizations allow them to log in with the SolarWinds Unified Login credentials, the user can log in once to access all of their organizations.
What happens if I remove a user from my organization’s IdP?
If a user leaves your organization and is removed from your IdP, the user’s access to your organization and its data is revoked. However, if the user was defined as a service account, their service account status will still allow them to access the organization. Remove the user account from the list of service accounts to ensure access to your organization is revoked.
While the user’s access to your organization and its data is revoked, it is still listed as a member of the organization in the Users page of the Organization Settings but has no products enabled. See Remove a user from your organization for more information.