PostgreSQL Logs
Loggly provides the infrastructure to aggregate and normalize log events so they are available to explore interactively, build visualizations, or create threshold-based alerting. In general, any method to send logs from a system or application to an external source can be adapted to send logs to Loggly. The following instructions provide one scenario for sending logs to Loggly.
You can send PostgreSQL logs to Loggly over syslog. Your syslog daemon such as rsyslog will receive these events and then forward them to Loggly. The advantage of Rsyslog is that it can send TCP events without blocking your application, can optionally encrypt the data, and even queue data to add robustness to network failure.
PostgreSQL Logging Setup
1. Configure Syslog Daemon
If you haven’t already, run our automatic Configure-Syslog script below to setup rsyslog. Alternatively, you can Manually Configure Rsyslog or Syslog-ng.
curl -O https://www.loggly.com/install/configure-linux.sh sudo bash configure-linux.sh -a SUBDOMAIN -u USERNAME
Replace:
- SUBDOMAIN: your account subdomain that you created when you signed up for Loggly
- USERNAME: your Loggly username
2. Configure Syslog Daemon for UDP Input
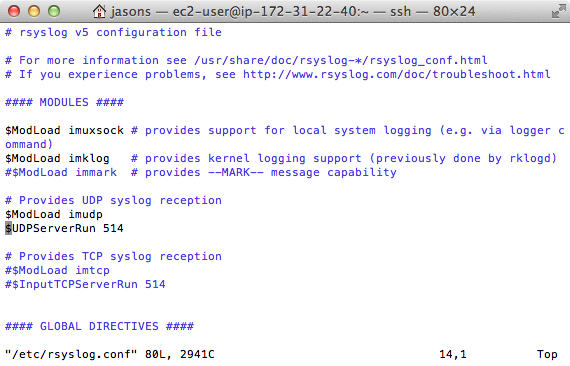
Open rsyslog’s configuration file
sudo vim /etc/rsyslog.conf
Uncomment these lines to accept UDP messages on the default port 514.
$ModLoad imudp $UDPServerRun 514
Restart the rsyslog service so the changes take effect
sudo service rsyslog restart
3. Configure PostgreSQL to send logs to Syslog
Open postgresql.conf file to send PostgreSQL logs to syslog.
sudo vim /etc/postgresql/9.3/main/postgresql.conf
Update the following configuration
log_destination = 'syslog'
Restart PostgreSQL
/etc/init.d/postgresql restart
4. Verify Events
Search Loggly for events with the appName as postgres or using tags. If if doesn’t work, see the troubleshooting section below.
syslog.appName:postgres or using the tags you have used.
Advanced PostgreSQL Logging Options
- Log File Monitoring – If you log to file, you can send these files to Loggly.
Troubleshooting PostgreSQL Logs
- Wait a few minutes in case indexing needs to catch up.
- Check if you have restarted rsyslog service
- Run "sudo tcpdump -i lo -A udp and port 514″ to verify UDP events are being sent to localhost
- Search or post your own PostgreSQL logs questions, or other questions around Amazon RDS, database log files, or an instance running in the community forum.
The scripts are not supported under any SolarWinds support program or service. The scripts are provided AS IS without warranty of any kind. SolarWinds further disclaims all warranties including, without limitation, any implied warranties of merchantability or of fitness for a particular purpose. The risk arising out of the use or performance of the scripts and documentation stays with you. In no event shall SolarWinds or anyone else involved in the creation, production, or delivery of the scripts be liable for any damages whatsoever (including, without limitation, damages for loss of business profits, business interruption, loss of business information, or other pecuniary loss) arising out of the use of or inability to use the scripts or documentation.
